

Philippe Abdoulaye is a renowned digital transformation and information technology executive with strong track-record of transforming large technology organizations, building innovative digital solutions, and driving business impact. Strong background in leading transformations, mergers and acquisitions, channel digitization, and technology innovation.
An author of 8 books and more than 100 articles, founder of the e-learning platform The Digital IT Academy, a Rackspace Partner and member of Amazon Partner Network (APN), he helps IT organizations to transform their service management practices in domains such as Cloud Computing, IT as a Service (ITaaS), DevOps, AIOps, and IT Operating Models.
He's been:
1. Named among and rewarded as one of the top 20 cloud computing book sellers of all time by The Book Authority
2. Featured on Forbes, ZDNet, Inc, and foreign magazines like German ComputerWoche
3. Translated in French, Spanish, German, Chinese and cited in numerous digital transformation works
Forbes magazine has referred to him as a top prolific writer and speaker, He's the author of 7 books on Cloud Computing, IT as a Service (ITaaS), DevOps, and Platform Business Models. He gives keynote speeches and executive workshops around the globe on how to properly leverage cloud computing and DevOps technologies to generate business revenue.
Philippe currently authoring a book and online training on Amazon Web Services (AWS) for digital business challenges to be published by Wiley in 2021.
Available For: Consulting, Speaking
Travels From: Raleigh, NC
Speaking Topics: AWS Cloud & DevOps
| Philippe Abdoulaye | Points |
|---|---|
| Academic | 0 |
| Author | 221 |
| Influencer | 20 |
| Speaker | 30 |
| Entrepreneur | 0 |
| Total | 271 |
Points based upon Thinkers360 patent-pending algorithm.
 The Illusion of Transformation: Why Solution Architecture Won’t Save the Enterprise
The Illusion of Transformation: Why Solution Architecture Won’t Save the Enterprise
Tags: Cloud, DevOps, Digital Transformation
 Data Analytics: The Amaris Data Governance Initiative
Data Analytics: The Amaris Data Governance Initiative
Tags: Analytics, Cloud, Digital Transformation
 Recession's Impacts on IT Organizations: Reasons to Join Amaris' Cloud Practice Team
Recession's Impacts on IT Organizations: Reasons to Join Amaris' Cloud Practice Team
Tags: Cloud, Digital Transformation
 Cloud Experts Scarcity: The Secret Behind Amaris AWS Consultants
Cloud Experts Scarcity: The Secret Behind Amaris AWS Consultants
Tags: Cloud, Digital Transformation, Innovation
 What The CIO's Crystal Ball Says About The 2023 IT Trends
What The CIO's Crystal Ball Says About The 2023 IT Trends
Tags: Cloud, Digital Transformation, Innovation
 L'actualité Cloud chez Amaris Jobs, Articles, Services Cloud Innovants ...
L'actualité Cloud chez Amaris Jobs, Articles, Services Cloud Innovants ...
Tags: Cloud, DevOps
 Lifting the Veil on Amaris Cloud Migration Framework: The AWS Extended EC2 Design Pattern
Lifting the Veil on Amaris Cloud Migration Framework: The AWS Extended EC2 Design Pattern
Tags: Cloud
 Cloud Transformation : The Keys to Avoid Failures and Succeed
Cloud Transformation : The Keys to Avoid Failures and Succeed
Tags: Cloud, Digital Transformation, Leadership
 Découvrez les Services d'Audit Cloud d'Amaris
Découvrez les Services d'Audit Cloud d'Amaris
Tags: Cloud, Digital Transformation, Leadership, DevOps
 How to Thrive in the Covid-19 Recession by Going Digital Using SCENARIO
How to Thrive in the Covid-19 Recession by Going Digital Using SCENARIO
Tags: Business Strategy, Business Continuity, COVID19, Ecosystems
 Survivre à la Récession liée au COVID-19 en mettant son Activité au Diapason du Numérique
Survivre à la Récession liée au COVID-19 en mettant son Activité au Diapason du Numérique
Tags: Digital Transformation, Innovation, COVID19
 Learning AWS The Easiest & Quickest Way: The Framework
Learning AWS The Easiest & Quickest Way: The Framework
Tags: Cloud, Data Center
 AWS DevOps Implementation: The XP and CodePipeline Integration Pattern
AWS DevOps Implementation: The XP and CodePipeline Integration Pattern
Tags: Cloud, Innovation, DevOps
 DevOps Implementation: The XP and AWS CodePipeline Integration Pattern
DevOps Implementation: The XP and AWS CodePipeline Integration Pattern
Tags: Innovation, Agile, COVID19
 Transforming IT for the COVID-19 Disrupted Business Context
Transforming IT for the COVID-19 Disrupted Business Context
Tags: Business Continuity, COVID19
 Cloud Made Simple for Undecided Career Change Planners - Part 1
Cloud Made Simple for Undecided Career Change Planners - Part 1
Tags: Cloud
 IT Career Change: How to Make Your Digital Move Swift and Successful
IT Career Change: How to Make Your Digital Move Swift and Successful
Tags: AI, Cloud, Digital Disruption
 How CIOs Can Reinvent The IT Organization with Cloud Computing
How CIOs Can Reinvent The IT Organization with Cloud Computing
Tags: Agile, Cloud, Digital Transformation
 Amazon Web Services: Practices That'll Make Your AWS Migration Successful
Amazon Web Services: Practices That'll Make Your AWS Migration Successful
Tags: Cloud
 Beyond Facilitation: The Strategic Role of the MCSI
Beyond Facilitation: The Strategic Role of the MCSI
Tags: Cloud, DevOps, Digital Transformation
 Ranked #1 AWS Book for Executives in 2025— and Here’s Why It Matters for AI
Ranked #1 AWS Book for Executives in 2025— and Here’s Why It Matters for AI
Tags: Cloud, DevOps, Digital Transformation
 AI 2026 Decoded: What Leaders Must Get Right — or Get Left Behind
AI 2026 Decoded: What Leaders Must Get Right — or Get Left Behind
Tags: Cloud, DevOps, Digital Transformation
 AI Adoption Fails for One Simple Reason: We Confuse Technology with Leadership
AI Adoption Fails for One Simple Reason: We Confuse Technology with Leadership
Tags: Cloud, DevOps, Digital Transformation
 Turning AI Setbacks into High-Value Capabilities
Turning AI Setbacks into High-Value Capabilities
Tags: Cloud, DevOps, Digital Transformation
 Turning AI Setbacks into High-Value Capabilities
Turning AI Setbacks into High-Value Capabilities
Tags: Cloud, DevOps, Digital Transformation
 AI-Ready IT Leaders: ESGI and AWStraight France in Action
AI-Ready IT Leaders: ESGI and AWStraight France in Action
Tags: Cloud, DevOps, Digital Transformation
 AI Won't Work If We Repeat the Same Cloud Mistakes
AI Won't Work If We Repeat the Same Cloud Mistakes
Tags: Cloud, DevOps, Digital Transformation
 Why Businesses Struggle to Innovate—And How XGenAI Fixes It
Why Businesses Struggle to Innovate—And How XGenAI Fixes It
Tags: Cloud, DevOps, Digital Transformation
 Unveiling AI / ML 2025: Expect a Gold Rush Toward Generative AI.
Unveiling AI / ML 2025: Expect a Gold Rush Toward Generative AI.
Tags: Cloud, DevOps, Digital Transformation
 The AI Hysteria: Why AI Leadership Holds the Key to Success
The AI Hysteria: Why AI Leadership Holds the Key to Success
Tags: Cloud, DevOps, Digital Transformation
 Shifting from Enterprise Architecture to Enterprise Cloud: A Holistic Approach to Cloud Computing
Shifting from Enterprise Architecture to Enterprise Cloud: A Holistic Approach to Cloud Computing
Tags: Cloud, Digital Transformation, Ecosystems
 Tackling AI Adoption: Why AWS Technologies Should Be Your Choice
Tackling AI Adoption: Why AWS Technologies Should Be Your Choice
Tags: Cloud, Digital Transformation, Customer Experience
 AI Adoption: The Critical Role of AWS Training in Addressing Enterprise AI/ML Challenges
AI Adoption: The Critical Role of AWS Training in Addressing Enterprise AI/ML Challenges
Tags: AI, Cloud, Digital Transformation
 Update: Introducing My New Monthly Newsletter "Transform Your IT with AWS and AI"
Update: Introducing My New Monthly Newsletter "Transform Your IT with AWS and AI"
Tags: Cloud, DevOps, Digital Transformation
 Amaris AWS Big Data Solution: How Managing Complexity Reverses Success Rate to 100%
Amaris AWS Big Data Solution: How Managing Complexity Reverses Success Rate to 100%
Tags: Analytics, Cloud, Digital Transformation
 Transforming Your Business with AWS: Getting the Most Out of Using AWS to Modernize and Innovate Your Digital Services
Transforming Your Business with AWS: Getting the Most Out of Using AWS to Modernize and Innovate Your Digital Services
Tags: Cloud, Digital Transformation, Project Management
 The Complete ITaaS Delivery Model
The Complete ITaaS Delivery Model
Tags: Cloud, Digital Transformation, DevOps
 Cloud Computing: Advanced Business and IT Strategies
Cloud Computing: Advanced Business and IT Strategies
Tags: Cloud, Digital Disruption, Digital Transformation
 Most Outstanding in Digital Transformation Advisory 2019
Most Outstanding in Digital Transformation Advisory 2019
Tags: Cloud, Digital Transformation, Agile
 Best-Selling Cloud Computing eBooks of All Time
Best-Selling Cloud Computing eBooks of All Time
Tags: Agile, Cloud, Digital Transformation

Tags: Agile, Cloud, Digital Transformation
Tags: Digital Transformation, Agile, DevOps
 Reinventing the Business with IT Innovations for the Digital Age
Reinventing the Business with IT Innovations for the Digital Age
Tags: Agile, Cloud, Digital Transformation
 ITaaS: The Future of the CIO
ITaaS: The Future of the CIO
Tags: Cloud, Digital Transformation, Agile
 Yes, DevOps is all about business growth, especially the digital variety
Yes, DevOps is all about business growth, especially the digital variety
Tags: Cloud, Agile, DevOps
 IT as a Service: Was CIOs dafür tun müssen
IT as a Service: Was CIOs dafür tun müssen
Tags: Cloud, Digital Transformation, Digital Disruption
 Implementing Enterprise Cloud Security: The Cybersecurity Fortress Design Pattern
Implementing Enterprise Cloud Security: The Cybersecurity Fortress Design Pattern
The accelerated penetration of digital business and the adoption of cloud computing and related technologies including IoT, AI, big data, and DevOps go hand in hand with the ever-increasing cyber threats inflation. As paradoxical as this may sound, the adoption of these technologies and the IT transformations that go with it introduce new security vulnerabilities. The best answer is certainly not the isolated implementation of the latest tools as is too often the case, but the deployment of what is increasingly referred to as Enterprise Cloud Security. It makes business leaders both proactive and responsive to cyberattacks. In the following, I discuss the Cybersecurity Fortress Design Pattern that I developed to implement enterprise cloud security.
Enterprise Cloud Security refers to how well people, policies, procedures, processes and security tools are deployed throughout the organization in a way that effectively protects the company's IT including cloud and on-premise operations, critical systems and data from internet attacks. Despite the fact that cloud security and in general cybersecurity has become a key business issue, an impressive number of companies that have adopted cloud computing have experienced cloud-related security incidents, about 80% of them, according to many well-informed reports.
The most common cloud security incidents according to CloudTech's Duncan MacRae in a study that involved a panel of major cloud adopters include:
I totally agree with the findings, they are the same as I have been observing for 13 years. My conviction is that the root cause of these cloud security issues is the fact that systemic and holistic approaches to managing cybersecurity are ignored in favor of piecemeal processes. It is why I developed the Cybersecurity Fortress Design Pattern.
The cybersecurity fortress design pattern seeks to help businesses to rapidly implement robust cyber fortresses. It builds on the NIST Cyber Security Framework (CSF) to provide the methodological, operational, and organizational framework needed to effectively manage cybersecurity risks and proactively prevent or respond to cyberattacks.
The cybersecurity fortress pattern is based on five principles that determine the mindset as well as the organizational, operational, and technological pillars needed to design and implement cybersecurity fortresses. They include:
The design of enterprise cloud security fortresses should follow these five principles.
The above figure gives an overview of the enterprise cloud architecture and how cybersecurity fits into the company's IT. It highlights five cybersecurity building blocks derived from the NIST Cyber Security Framework (CSF) five core functions including Identify, Protect, Detect, Respond, and Recover. Each encapsulates specific cybersecurity processes, activities, staff, skills, methodologies, and tools.
Let's discuss them further!
Identify - In connection with principles 1, 2, and 3, the challenge here is to deploy a system of people, processes, and tools that allows the company to have a 360 degree view of its enterprise architecture and IT infrastructure so that it is able to proactively spot and evaluate cyber risks and determine preventive actions. The bottom line is to get current and future threats, both internal and external, clearly identified and documented. Key activities in this building block include governance, asset management, and risk management.
Protect - Relating to principles 4 and 5, the core purpose in this building block is to perform preventive cybersecurity controls in well-determined human, organizational, operational, and technological circumstances. The focus is on identity management and access controls and what's expected is to get remote access controlled. Key activities include identity management and access control, awareness and training, data security, information security protection processes and procedures, maintenance. Popular Preventive Solutions (procedures, policies, controls and tools) supporting this building block's activities include Authentication & Authorization, Firewalls, Malware Protections, VPN, MFA, SSO, and Cryptography.
Detect - Relating to principle 4 as well, this building block stresses security continuous monitoring through performance of detective cybersecurity controls in well-determined human, organizational, operational, and technological contexts. The objective is to get vulnerabilities scans continuously performed. Key activities include security continuous monitoring and anomalies and events continuous based on detection processes. Common Detective Solutions (procedures, policies, controls and tools) supporting the Detect building block include Events and Anomalies Monitoring, Intrusion Detection Systems (IDS), Security Information and Event Management Systems (SIEMs), User and Entity Behavior Analytics Systems (UEBAs), Threat Hunting Systems, and Antivirus Software.
Respond - Addressing principles 4 and 5, the focal point in this building block is to perform reactive cybersecurity controls following analysis and understanding cyber attack contexts. The goal is to make sure forensics are performed. Key activities include analysis, response planning, communications, mitigations, and improvements. Usual Reactive Solutions (procedures, policies, controls and tools) include Incident Response Plan (IRP), Computer Security Incident Response Team (CSIRT), and IDS Logs Analysis Tools.
Recover - In connection with principles 4 and 5, this building block is concerned with recovering from cyberattacks. The bottom line is to get recovery plans executed as needed. Key activities include recovery planning, communications, and improvements. Familiar Recovery Solutions (procedures, policies, controls and tools) include Recovery Plans, Disaster Recovery, and Backup & Recovery.
Those familiar with it has probably guessed that deploying enterprise cloud security is about implementing the NIST CSF recommendations.
Implementing the organizational, operational and technological framework in which technical experts will express their ingenuity to protect the company's assets is the first thing you must have in mind. It is the purpose of the 4 stages of the Cybersecurity Fortress Pattern:
The goal in this step is to identify and understand the gaps between the as-is environment and the enterprise cloud security architecture from the cybersecurity fortress pattern's perspectives. Key activities include (1) putting together the as-is enterprise architecture including people, processes, methodologies and tools; (2) benchmarking the as-is enterprise architecture against the cybersecurity fortress architecture elements; (3) identifying the gaps along with the related vulnerabilities; and (4) making cybersecurity improvement recommendations.
The stake in this step is to fill the gaps identified in the audit to design the to-be enterprise cloud security platform and align it, as much as possible, to the agreed upon cybersecurity fortress pattern's recommendations. Primary activities include (1) identifying / designing cybersecurity solutions likely to fill the identified gaps; (2) reconfiguring the as-is cybersecurity architecture into the to-be cybersecurity architecture from the people, processes, procedures, policies, and tools perspective; and (3) develop the cybersecurity fortress deployment plan.
In this step the goal is to deploy your cybersecurity people, processes, procedures, policies, and tools throughout your organization. The principal activities include (1) communicating about the changes ahead, (2) training to the to-be cybersecurity responsibility assignment (RACI) matrix, processes, procedures, policies, and tools across the organization; and (4) running a cybersecurity pilot project.
The ever-increasing number of cyberattacks, +38% in 2022 compared to 2021, leaves no room for improvisation; CIOs would be wrong to persist in blind cybersecurity implementations that stress blind deployments of tools. Furthermore, their incredible plurality and accelerated frequency make it suicidal to cling to this one-eyed view of cybersecurity. Enterprise architecture approaches are required as they provide the tools (cartography of applications, systems, and processes, enterprise architecture governance, etc) that help to make the implementation of cyber fortresses easier and faster.
Additional benefits of the fortress design pattern include:
Stay tuned, I will soon launch the initiative, The AWS Cybersecurity Fortress Project. In the same spirit as my book "Transforming Your Business with AWS," this international community of experts that we will build together will share Enterprise Cloud Security best practices with a view to deliver a formal and complete AWS Cybersecurity Fortress Models.
Tags: Cloud, Cybersecurity, Business Continuity
 Cloud Migration : Why Opposing Thinkers and Doers is a Major Failure Factor
Cloud Migration : Why Opposing Thinkers and Doers is a Major Failure Factor
Many #cloud migrations fail because they're led by doers, not thinkers; conductors are needed.
I wrote this post to share the unspoken reasons why today's cloud migration projects fail to deliver the expected business benefits.
Contrary to the widespread opinion, I won't blame solutions architects and cloud engineers but the erroneous practice that's been stressing technology implementation at the expense of broader perspectives.
Let's be serious, do you think that, what boards of directors expect from the money invested in #cloudcomputing initiatives, is the hurrah of a successful app migration team? The answer is, "No!" What's expected is, transformed business ready to tackle #digital challenges, what's expected is substantial ROIs measured in dollars.
Let's be clear about it, technology alone doesn't make profitable business; people skilled to cloud operational models, agile operational models supporting key IT processes, practices, and tools, well-architected landing zone and application aligned to cloud-native standards are the success ingredients.
Adapting the business for the digital competition is the goal of any cloud migration initiative.
Migrating IT to the cloud is like building the Brooklyn Bridge, the analogy isn't exaggerated; there are goals, stakes, tons of challenges, multiple methodologies, tools and competencies to orchestrate.
That's why opposing, "thinkers vs doers" is a total nonsense. Suggesting that doers (solutions architect and cloud engineers) is all that's needed is like suggesting that, workers alone, without plans, with their sole bolts, screws, and screwdrivers built the Brooklyn Bridge.
Building the Brooklyn Bridge, a master piece of 139 years old, took Visionaries :
- Owning the big picture (vision)
- Developing building plan and scenarios (roadmap)
- Organizing building effort (timelines, team, tasks, and RACI)
- Directing rigorously (project management) building activities
- Informing the population (pilot project, operational model deployment, training)
As you can see, opposing, "thinkers vs doers" does not make sense.
Thinkers are essential, they're the conductors that put together the conditions for success and smartly juggle with them across the cloud adoption journey to make the cloud migration project a successful business initiatives.
I'm an experienced cloud transformation director, cloud migration director, enterprise architecture director, call it whatever you want, but transforming IT with the cloud is what I'm good at, what I love doing, it's what I've been doing at Amaris Consulting
I'm proud official #aws hero, ranked in the global Top 10 cloud thought leaders and influencers, my AWS migration handbook, "Transforming Your Business with AWS" is ranked #1 in the IT books to read in 2022.
There's a lot we can share about your cloud initiative.
Email me : philippe.abdoulaye@amaris.com
Stay tuned, next week, I'll share, "The Value of Cloud Migration PMO and Cloud Center of Excellence
Tags: Cloud, Digital Transformation, DevOps
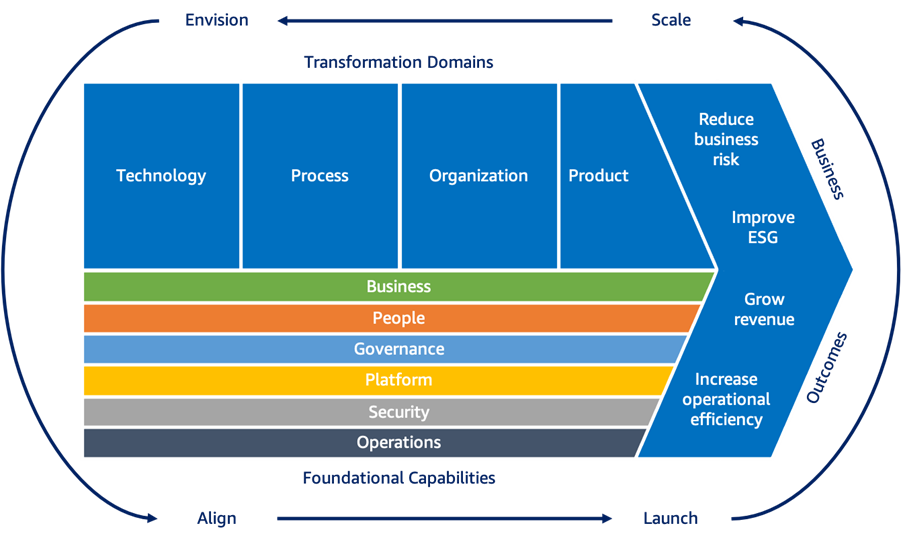 Why AWS Cloud Adoption Framework (CAF) 3.0 Will Revolutionize Cloud Transformation Practices?
Why AWS Cloud Adoption Framework (CAF) 3.0 Will Revolutionize Cloud Transformation Practices?
In 2022, the #aws Cloud Adoption Framework (CAF) 3.0 will prove to be the tool that CIOs have been desperately waiting for to successfully transform their #enterprisearchitecture to the cloud and help their business lines to succeed in the growing digital economy.
The fact is, too many businesses are still struggling to enjoy the promised benefits of #cloudcomputing . The many reasons include transformation perspectives that restrictively stress IT at the expense of the business, lack or inefficient cloud vision and strategy, undefined or dysfunctional cloud adoption journey, and many other factors that prevent to properly design this central piece of the digital company's value chain: The Enterprise Cloud Ecosystem.
In addition to clearly setting the business goal, helping the business transform to meet the digital economy disruptive challenges, the AWS CAF 3.0 provides three powerful elements:
- Macroscopic cloud transformation journey (Envision, Align, Launch, Scale) that could serve as the baseline for developing flexible and powerful cloud adoption strategies.
- Four areas of focus ( #technology , Process, Organization, Product) acting as enablers of the expected business value.
- Six foundational capabilities (Business, People, Governance, Platform, Security, Operations) whose combinations are likely to provide unexpected competitive advantages needed to make any digital business prosperous.
Over the next few weeks I'll be going into more details about AWS CAF 3.0 and how we combine it with the Hybrid & Multi-Cloud Enterprise Cloud Design Pattern to help businesses achieve accelerated digital transformation successes.
I urge CIOs and technology leaders, whether they use AWS or not, to take a look at the AWS CAF 3.0. Great Job Jeff Barr, AWS CAF 3.0 will revolutionize in the short term cloud transformation practices. That's my conviction.
Tags: Cloud, DevOps, Digital Transformation
 180 Days Immersed in The AWS Universe: How J&S Food Went Digital
180 Days Immersed in The AWS Universe: How J&S Food Went Digital
New Day, CNN's morning TV show, was discussing the digital platform economy and the case of a company that weirdly caught my attention; since the beginning of the week, a curious gut feeling was urging me to investigate digital transformation scenarios similar to that of this company. I could not understand why.
Christine Romans, the TV show host, was telling the story of J&S Food Inc., a leading firm in the global food industry. The company was losing market shares and money; the platform economy's expansion in the food sector brought in new competitors including Amazon Fresh, Fresh Direct, Instacart, and Growcer. Their new food shopping experience—online food shopping, virtual supermarkets, smart shopping carts—disrupted the industry and by extension, made many aspects of the company irrelevant particularly, its business model and more importantly its IT.
"J&S Food? that name sounds like a mystery," I whispered. I stood and opened the curtain; Capital Boulevard in downtown Raleigh was under the rain. "Perfect weather for staying home and dig on AWS cybersecurity," I whispered again when my smartphone suddenly rang. It read, "J&S Food, Hoboken, NJ." Confused by the strange coincidence, I picked up the call.
In a French accent that I recognized immediately, Jean-Pierre introduced himself as the J&S Food's CIO. After the greeting and civilities, he went straight to the point, "I know your work on AWS, I love it. I've attended your conference in Hamburg, I've even read your latest book Transforming Your Business with AWS: Getting the Most Out of Using AWS to Modernize and Innovate Your Digital Services. (John Wiley & Sons). A master piece. I need your help."
Delighted by these morning compliments, but above all, troubled by the gut feeling that J&S Food would get in touch, I stuttered, "How... How... can I help you?" Enthusiastic, Jean-Pierre replied, "To survive, J&S Food must go digital. We want you to team up with our Enterprise Architect to help us achieve it."
Two hours later, the Webex meeting between Jean-Pierre, Wei, and me took place. The next day we kicked off J&S Food's digital transformation project.
I was leading AWS engagements for almost 14 years, and was known for easing complex AWS migrations using agile methodologies. My record included datacenter migrations to cloud, digital transformations, and the development of highly innovative digital products based on Machine Learning (ML) and Internet of Things (IoT). On the other hand, Wei, the Singapore-born enterprise architect, had a different profile; for nearly 21 years, he advised CIOs on how to leverage IT to boost business profits. SAP's Kaan Turnali's quote, "Digital transformation isn't a technology makeover, it's a business revolution," summarized Wei's digital transformation doctrine.
The big question was, how we would go about it? Wei and I agreed on the team and on using scrum as the framework to support the digital transformation effort. I tended to use Jira Scrum as a lightweight framework for managing projects with aggressive deadlines and complex requirements by augmenting its delivery lifecycle's steps with varied tools and methodologies as deemed as necessary. These augmented steps made the transformation effort iterative and incremental, they included:
This educational and learning article about AWS Digital Transformation tells the unprecedented story of how an Enterprise Architect and an AWS Digital Transformation Strategist teamed up to help a global firm to restore its competitiveness.
“ Tackle Your Business Model Transformation Issue First Or Prepare To Completely Fail
Wei was one of the few enterprise architects claiming that making the business model transformation the starting point of the digital transformation project is creating the conditions for success. "Business first, technology next," was his mantra. He was right, the chief goal is to adjust the way the company does business to the requirements of the digital competitive environment, and certainly not the ill-considered deployment of technologies that the company doesn't necessarily need. Experience shows that most companies engaged in digital transformation with in mind the belief that, alone technology deployment mechanically boosts benefits, fail to generate the expected revenues.
As he walked to the paperboard at the back of the meeting room, he recalled the strategic planning process complexity, "the challenge is to establish a roadmap that not only brings out the organizational, operational, and technological changes to implement, but that also tells how and when to implement these changes."
Under the watchful eye of the meeting participants, he drew a diagram which depicted a two-step digital business transformation planning process including redesigning the business model which was about designing the business solution that would help the company to meet its digital challenges and planning the business transformation which was about developing the company's digital transformation roadmap.
Using a collaborative approach involving the marketing and sales representatives, based on three questionnaires—industry analysis, business impacts analysis, digital strategy map—Wei identified the changes in the food industry, spotted their impacts on J&S Food's business model, facilitated J&S Food's digital strategy development, and then derived the transformation solutions needed to adapt the company to the new competitive environment.
The decisions made as part of the digital transformation solutions included:
The intent of the smart shopping bag was to offer a superior food shopping experience by allowing customers to skip the checkout line in J&S Food's physical stores. They would save a precious time.
The roadmap that resulted from the discussions included three phases: Implementation, Experiment, and Deployment. They reflected J&S Food's digital transformation journey.
In a louder voice, as if to ask more attention, Wei explained, "As the roadmap translates it, the bottom line of our digital transformation strategy is to implement four digital business performance enablers including technology, operational model, organizational model, and people." As participants fell silent, he clarified, "About technology, our IT infrastructure including the ecommerce applications will migrate to AWS cloud to not only cut IT expenses but also to accelerate IT operations. It's good for our time-to-market and for our responsiveness to industry changes. With regard to the operational and organizational models, we'll deploy a Cloud Operating Model for AWS, Scrum Agile, and probably an Ecommerce Operating Model. And as for people, concerned IT and business staff will be either hired or trained to AWS, Agile, and digital business platform."
Waving his hands, as if willing to convince, Wei continued, "These digital business performance enablers will be implemented through three phases involving 8 sprints of 50 architecture, migration, software, and platform deployment activities. These phases include: Implementation concerned with their implementation, Experiment dedicated to their experimentation through a pilot a project, and Deployment focused on deploying enterprise-wide the final releases of the AWS cloud, applications, digital food platform, the smart shopping bag along with the operational and organizational models."
The magic with Wei's Digital Business Model Development framework, as astonished Jean-Pierre admitted it was that, "The combined application of the three questionnaires (industry analysis, impact analysis, and digital strategy map) made it possible to identify the food industry disruptors and pinpoint the impacted business aspects likely to be adjusted to the platform business requirements and digitized with technology."
“ Derive Your AWS Platform Architecture from Your Business Architecture Then Optimize it Using The AWS Well-Architecture Framework (WAF) Best Practices
Three days later, according to the roadmap instructions, it was my turn to contribute to J&S Food's digital transformation; I had to develop the AWS platform's architecture that would support the company's digital business. It's important to note that, by developing the J&S Food's digital business architecture, Wei did an important part of the job. He provided the logical (or functional) architecture that would serve as the baseline for developing the AWS cloud architecture.
The meeting room was set up so that everyone could easily see the one-page PowerPoint presentation that I prepared and hear me; participants were arranged in a semicircle in front of me. They included enthusiastic Jean-Pierre and Wei, brilliant IT operations director Laetitia, plus some 20-25 thrilled developers, IT and database (DB) admins. They attended the workshop as part of my commitment to transfer AWS knowledge.
After the greeting, I warned, "Designing a cloud architecture must be supported by business motives, that is how Wei's digital business architecture is fundamental." He smiled, hiding rather badly his pride.
As I displayed the one-page presentation, I said, "The process isn't that easy; it's an effort where the building blocks, functions, and features of the business architecture are iteratively and incrementally mapped to the AWS services likely to enable them. The resulting technical platform is then fine-tuned based on the architectural best practices of the AWS Well-Architected Framework (WAF) five pillars: operational excellence, security, reliability, performance efficiency, and cost optimization."
Participants were listening quite carefully, some were taking notes while others were capturing the displayed AWS architecture development framework with their smartphone.
The story told by the one-page presentation was that, developing AWS solution architectures takes two fundamental elements: the business architecture as the input and the AWS Cloud Architecture Framework (CAF) as the generator of the desired AWS solution architecture.
As illustrated, the digital business architecture as designed by Wei, recommended two platforms including the smart shopping bag system and the digital food platform as well as the use of microservices and containers to make easy and speedy the application development process. Speaking directly to the technical team, I clarified, "From the AWS solution architecture perspective, the business architecture is the formulation of cloud architectural expectations and requirements not only in terms of compute, storage, and network virtual capabilities but also in terms of security, reliability, performance efficiency, operational excellence, and cost optimization expectations."
Anticipating the technical team’s questions, I hastened to propose, "Let’s see how the AWS architecture engineering framework will make this highly complex process simple." The audience fell silent.
Read the rest of the article on LinkedIn: https://www.linkedin.com/pulse/180-days-immersed-aws-universe-how-js-food-went-philippe-a-abdoulaye
Tags: Cloud, Digital Transformation, Innovation
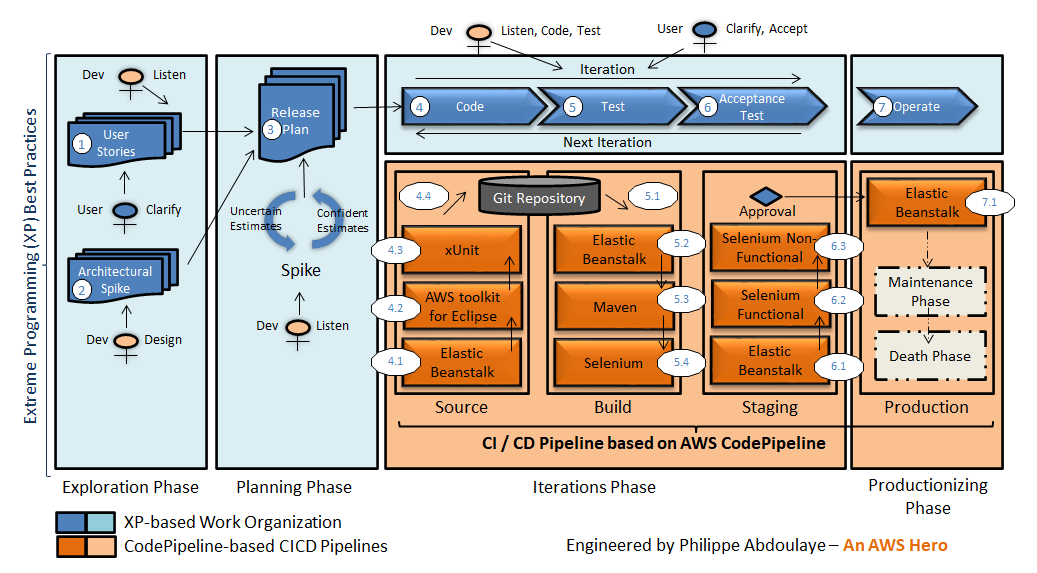 Accelerated DevOps Implementation: The XP and AWS CodePipeline Integration Pattern.
Accelerated DevOps Implementation: The XP and AWS CodePipeline Integration Pattern.
Tags: Agile, Cloud, COVID19
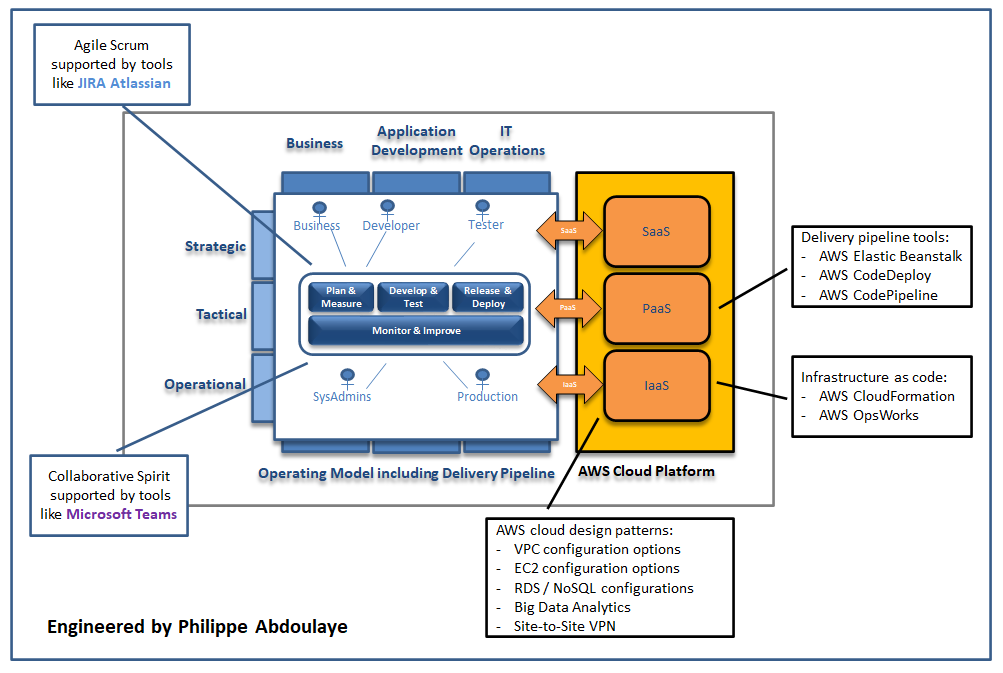 How to Transform IT for the COVID-19 Business Context
How to Transform IT for the COVID-19 Business Context
Tags: Agile, Cloud, Digital Transformation
 AWS Migration Strategy for Post Covid-19 / Covid-19 Era
AWS Migration Strategy for Post Covid-19 / Covid-19 Era
Location: New York, Charlotte, Remote Fees: $180 / hour
Service Type: Service Offered
 Beyond Facilitation: The Strategic Role of the MCSI
Beyond Facilitation: The Strategic Role of the MCSI Ranked #1 AWS Book for Executives in 2025— and Here’s Why It Matters for AI
Ranked #1 AWS Book for Executives in 2025— and Here’s Why It Matters for AI AI 2026 Decoded: What Leaders Must Get Right — or Get Left Behind
AI 2026 Decoded: What Leaders Must Get Right — or Get Left Behind