Mar21

In the wake of the 2021 cyber-attacks on energy infrastructure and utilities, and the heightened risk of cyber warfare being used in a more and more uncertain geopolitical landscape, we sit down with leading cybersecurity influencer and founder of Corix Partners JC Gaillard, to put things in perspective around IT and OT Security.
Historically, IT and OT belong to different worlds, or at least different parts of the enterprise.
If we look back, Operational Technology has always been typically air-gapped in the manufacturing sector, often running on proprietary hardware and software platforms. It belonged to the realm of plant and operations managers and was managed by them and their suppliers; it used to evolve on the same timeframes as plants and machinery.
Security and safety were always key components with OT but exploiting a vulnerability to cause harm was never that straightforward (although the air gap didn’t stop the Stuxnet attack 10 years ago…).
Patching vulnerabilities was often in the hands of the suppliers and stopping the plant or altering operations to apply a patch to prevent a low probability attack, was never high on the list of priorities for operations managers. Historically, there was never an OT Security concept as such; it was just part of designing manufacturing systems and running the plant.
Information Technology always evolved on different (shorter) cycles, compared to OT. Historically, it belonged to the realm of Head Office and the admin world in the manufacturing sector; but with the advent of the Internet and then the Cloud (and now remote working at scale since the COVID pandemic), the IT environment – and the supply chains it supports – have become more and more interconnected, and with hyper connection, came a significant increase in attack surfaces and associated cyber threats.
IT Security had to become more and more reactive in response, even if proactive defence-in-depth principles have continued to provide solid levels of security if properly applied across the depth and breadth of the enterprise.
That’s where the problems started with OT; because gradually the air gap between OT and IT was bridged, and it was bridged opportunistically – across industries – often to introduce point solutions, without any appreciation of the risks involved (potentially) and certainly without any kind of overarching picture or strategy.
And now, the technological acceleration coming with Industrial IoT sensors and 5G connectivity is in the process of taking this to a new level.
Overall, the IT/OT overlap was never structured, designed and secured as any kind of “interconnection”; for many, it just happened.
It did not result in the emergence of an OT Security strategy in the way there might have been an IT Security strategy; or in establishing an OT Security department, in the way there was an IT Security department.
In addition, OT devices and sensors rarely fit in any pre-defined IT box: Many are still proprietary; they’re not designed to run software agents in the way IT devices do, as Norton points out; they are often limited by their own architecture or the technological capacity of the legacy strata to which they belong.
As a result, they are not easy to integrate into a pre-existing IT Security Operations framework; they can be difficult to map out with precision and many end up ignored – but still connected to the wider IT network and potentially exposed to any threats it may carry.
Fundamentally, ownership around OT Security was rarely clarified in spite of its evolutions over the past decades and its growing dependency on IT: It is not rare for OT Security to end up in some form of organisational no-man’s-land, having become too hybrid and too complex for plant managers to handle and at the same time, too alien for IT Security managers to integrate properly into their practices.
The 2021 Colonial pipeline hack might have acted as an eye-opener for many manufacturing and energy firms, even if, in essence, it was not an attack on its OT systems.
Before jumping to tech solutions, clarifying ownership and governance around OT Security has to be the place to start for organisations finding themselves in that type of conundrum.
OT Security needs to be structured as a practice in itself, as part of a broader set of Cyber Security practices, and assigned roles, responsibilities and resources. It also has to be embedded across the business structure of the firm and its operational silos, in order to develop acceptance and trust with plant and operations managers.
Once the field is mapped out and the extent of the problem is assessed, ameliorative roadmaps can be drawn to build up OT Security levels, together with an effective and efficient interface with IT Security Operations; but as always it will involve action at process, people and technology level; and preferably in that order.
Keywords: Cybersecurity, Leadership, GRC
 Lateral Moves: The Most Overlooked Succession Strategy in Companies
Lateral Moves: The Most Overlooked Succession Strategy in Companies The Asset Play: Timing, Structure & Global Arbitrage
The Asset Play: Timing, Structure & Global Arbitrage 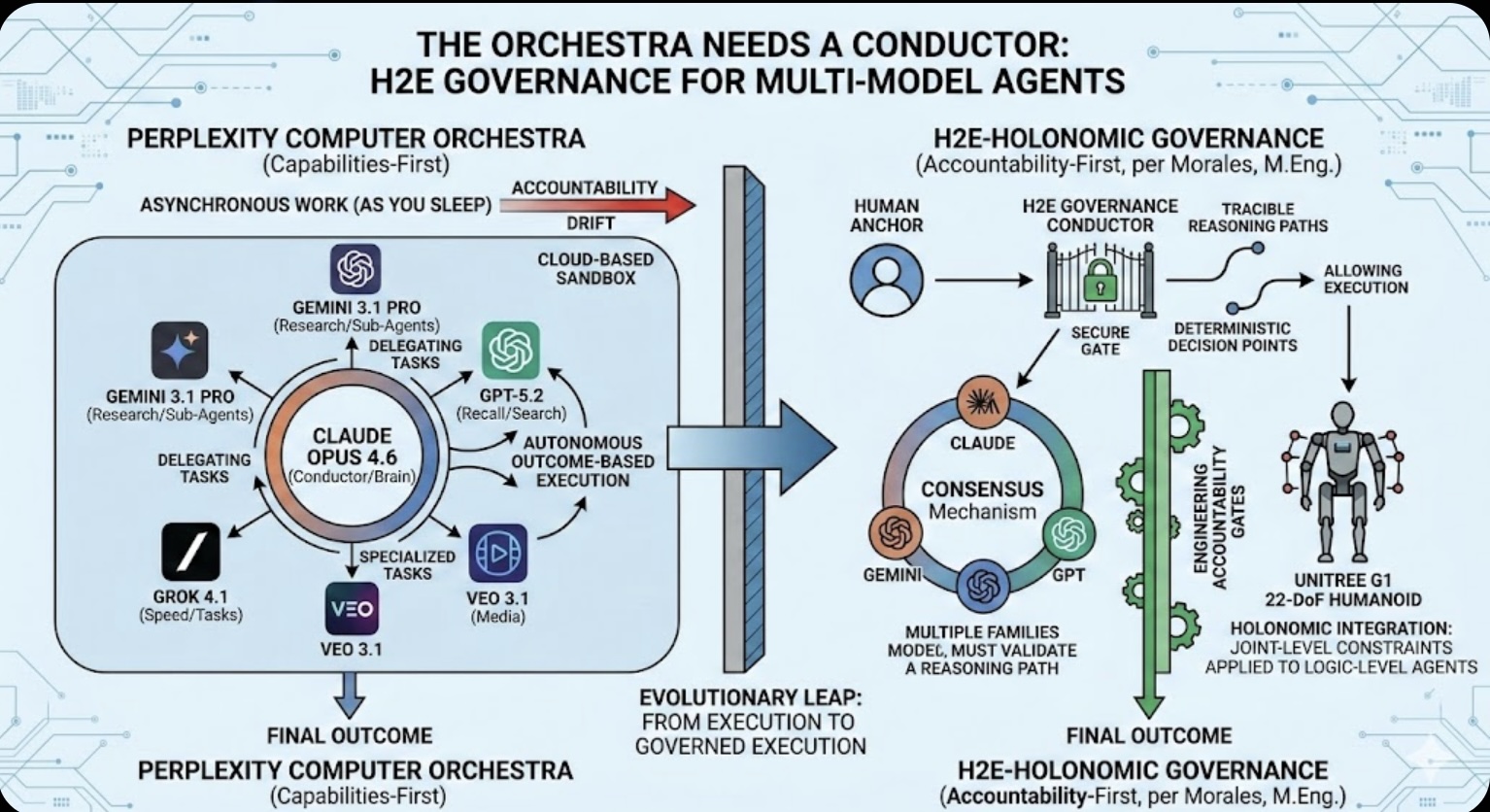 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business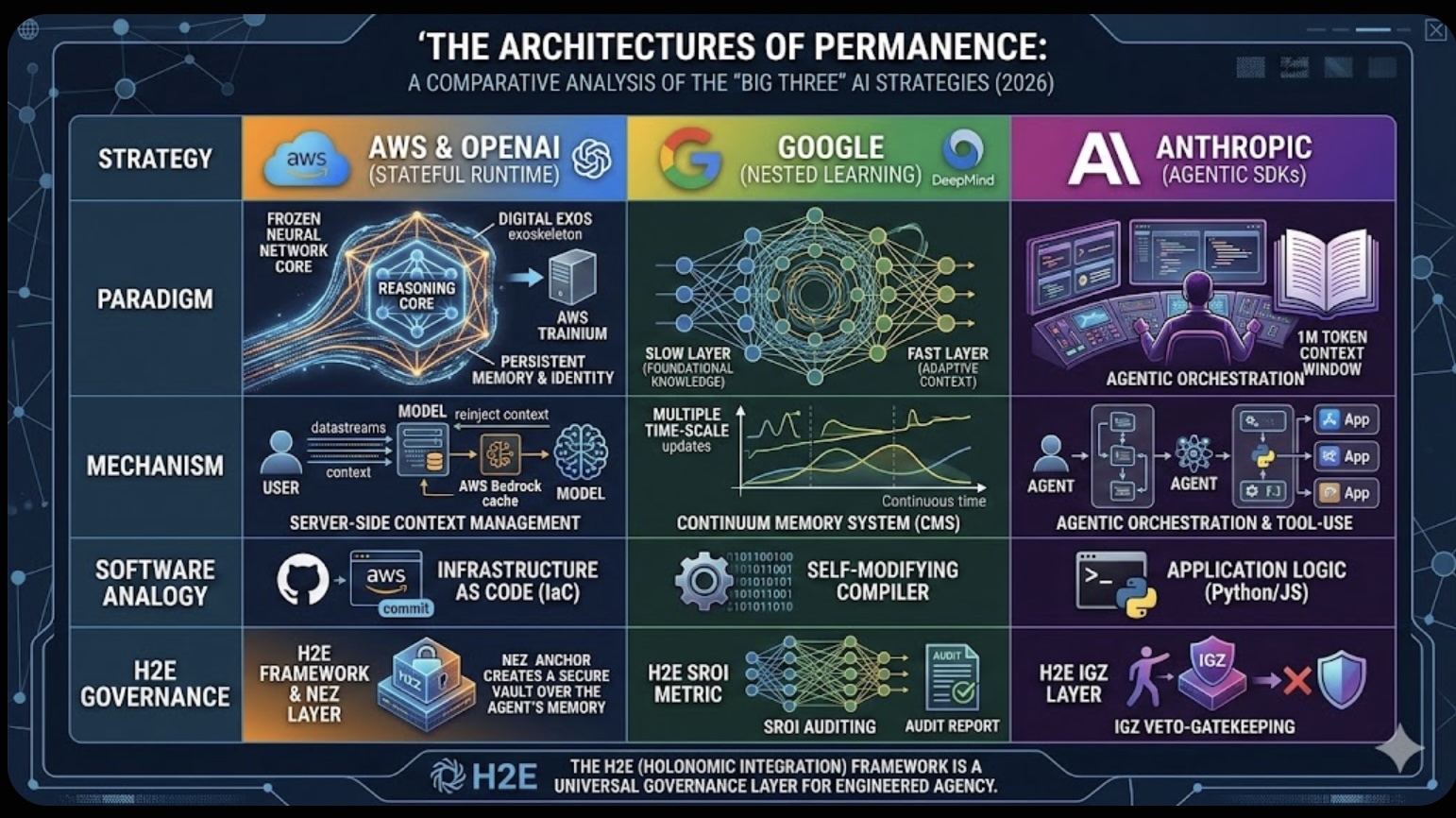 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)