Dec20

As we get deeper into the third decade of existence of cyber security practices, we take a look back at their evolution throughout the period with Corix Partners founder and global cybersecurity influencer JC Gaillard.
Where are priorities and levers now for CISOs? What should be the ideal profile of a new CISO? And how do you build up a change dynamics where cyber maturity is low?
The short tenure of the CISO continues to generate a vast amount of debate, aggravated by the COVID pandemic and the “great resignation” episode that it is inducing.
Looking beyond its reasons, the short tenure of the CISO raises another question: What do you actually achieve in 2 or 3 years in a complex and transversal field such as cyber security, and in particular in large firms?
One of my readers pointed out that some CISOs work precisely on those patterns because they are hired to put in place specific compliance alignment programmes, and they leave when the job is done, which typically involves those 2 to 3 years timeframes.
But what happens next? What guarantees can the business have that the next CISO will follow in the footsteps of the previous one? There are many ways to interpret and execute compliance requirements, and no doubt every cyber security professional has specific areas of expertise and particular pet subjects; it is not easy to step in and execute a programme of work designed by someone else.
In my view, the key around cyber security remains: Execution, Execution and Execution.
Knowing what to do is reasonably well established and cyber security good practice – at large – still protects from most threats, and still ensures a degree of compliance with most regulations.
Putting it in place, in real life, across the depth and breadth of the modern enterprise, is exactly where large firms have failed over the past 20 years, in spite of colossal investments in that space with tech vendors and large consultancies.
Large organisations morph constantly, either through mergers or organic expansion or their digital transformation (not mentioning major disruptive global events such as the 2008-2009 financial crisis or the COVID pandemic); business priorities and the perception of risk by the business shift accordingly, and they mechanically follow business cycles – which may be long or short – and the visibility those business cycles can afford to business leaders at any given time. Those dynamics are unavoidable.
But cyber security works on different patterns, in particular where maturity is low and real change is required to face escalating threats.
Very often, past execution failure in that space has left scars with senior execs. Some would have seen several generations of CISOs coming in with a grandiose transformative plan asking for millions, before disappearing after a few years, having achieved very little in practice in terms of real change.
The secret sauce for new CISOs will be in demonstrating that they can get things done over the right timeframes by manoeuvring around the political maze of large organisations and understanding how they really operate.
This is rarely about buying more tech, but more about understanding where the roadblocks are which have prevented progress in the past, how they link with the business culture of the firm and working out ways to remove or circumnavigate them.
It requires real life managerial experience, personal gravitas and political acumen, more than raw technical skills, because the CISO will not deliver change on their own – and cannot be expected to.
They will do it by leading a team of experts, influencing change and driving the execution of protective measures across the organisation and its supply chain.
More than ever, the key issue for the transformational CISO is time: It takes “the time it takes” to build the right team and drive the long-term dynamics of change around cyber security practices, across a more and more complex business environment also changing all the time, possibly on different cycles.
As well as business cycles, CISOs must be realistic around the perspective they give themselves to achieve change in order to place their role on the right trajectory over the mid to long-term; they must also be allowed and incentivised by their business to do so.
This is much harder than it might have been 10 or 15 years ago when the enterprise was more self-contained, and to keep a bond of trust with senior stakeholders, they must focus all the time on getting things done; not just over the short term, as inevitably tactical initiatives and firefighting requirements will emerge, but also strategically over the mid to long-term as part of a structured and coherent vision for the protection of the business endorsed by all from the Board down.
The times have gone when the CISO had to explain what cyber security was about and the value it brought
In the face of non-stop cyber-attacks, and the urgency of change around cyber security practices in large firms, the CISO has to be – first and foremost – a leader.
The role can no longer be limited to its technical content. Cyber security has a technical dimension of course, and a fundamental one, but it was never just about tech.
Delivering real and lasting change around cyber security across the complexity of large organisations has to involve all corporate silos: Business units, geographies and support functions, as well as IT and suppliers.
Bringing them all onboard with a common and coherent cyber security agenda cannot be something arbitrary or pre-determined.
It can only be built on the basis of the situation and priorities of all stakeholders: They will buy into it if there is something in it for them; they will resent it and drag their feet if it comes across as something arbitrary imposed by head office.
Understanding the firm’s governance dynamics – and frankly, the internal politics – will be key for any CISO in large organisations to calibrate the change agenda to a level the fabric of the business can tolerate.
That has to start by listening to key stakeholders, understanding their challenges and their priorities around cyber security, as well as the general situation of the business.
The times have gone when the CISO had to explain what cyber security was about and the value it brought. All business leaders would have been exposed to the concept of cyber threats and cyber attacks given the level of media coverage of the last decade. Many would have faced their impact in other roles. They will have a view on the matter, and quite often a balanced business view of what to do – or not – about it.
Too many CISOs jump straight at technical recipes or try to apply ready-made solutions they have used or seen elsewhere.
“What can I do to help you?” should be the opening question for the CISO in their exchanges with stakeholders.
Listening to the answers, accepting them for what they are (irrespective of the CISO’s personal inclinations), structuring them into a strategic change agenda, and – most importantly – delivering on the expectations created, are the pillars on which a successful CISO should build their practice (in particular, the incoming CISO).
Based on what we have highlighted so far in this discussion, we start to see emerging a profile of a certain type for the CISO, that will be key for the role to be successful.
The profile of an individual who has sufficient management experience and political acumen to navigate the complex governance waters of large firms, the ability to listen without jumping to a pre-determined agenda, and the ability to deliver on expectations in a complex and transversal field.
Where maturity is low and aggressive change is required around cyber security practices, those attributes are more important, in my view, than the native ability to understand the technology context in which cyber security is rooted.
Of course, those are attributes some technologists could develop naturally over the course of a career in tech, in particular in senior roles, but fundamentally, they are leadership attributes that come with time and experience.
The key for me is the quality of the listening and the building of some realistic and achievable consensus around the expectations collected from stakeholders, without always dropping to the lowest common denominator (generally, that’s awareness development in the cyber security space – whatever that means in practice…).
It’s a difficult task but it is the essence of true leadership.
Going back to the basic meaning of the word, a “leader” is someone who is followed; and people generally follow when have the sense they will get something in return.
Those are the simple dynamics successful CISOs have to build around cyber security.
Keywords: Cybersecurity, Leadership, GRC
 Lateral Moves: The Most Overlooked Succession Strategy in Companies
Lateral Moves: The Most Overlooked Succession Strategy in Companies The Asset Play: Timing, Structure & Global Arbitrage
The Asset Play: Timing, Structure & Global Arbitrage 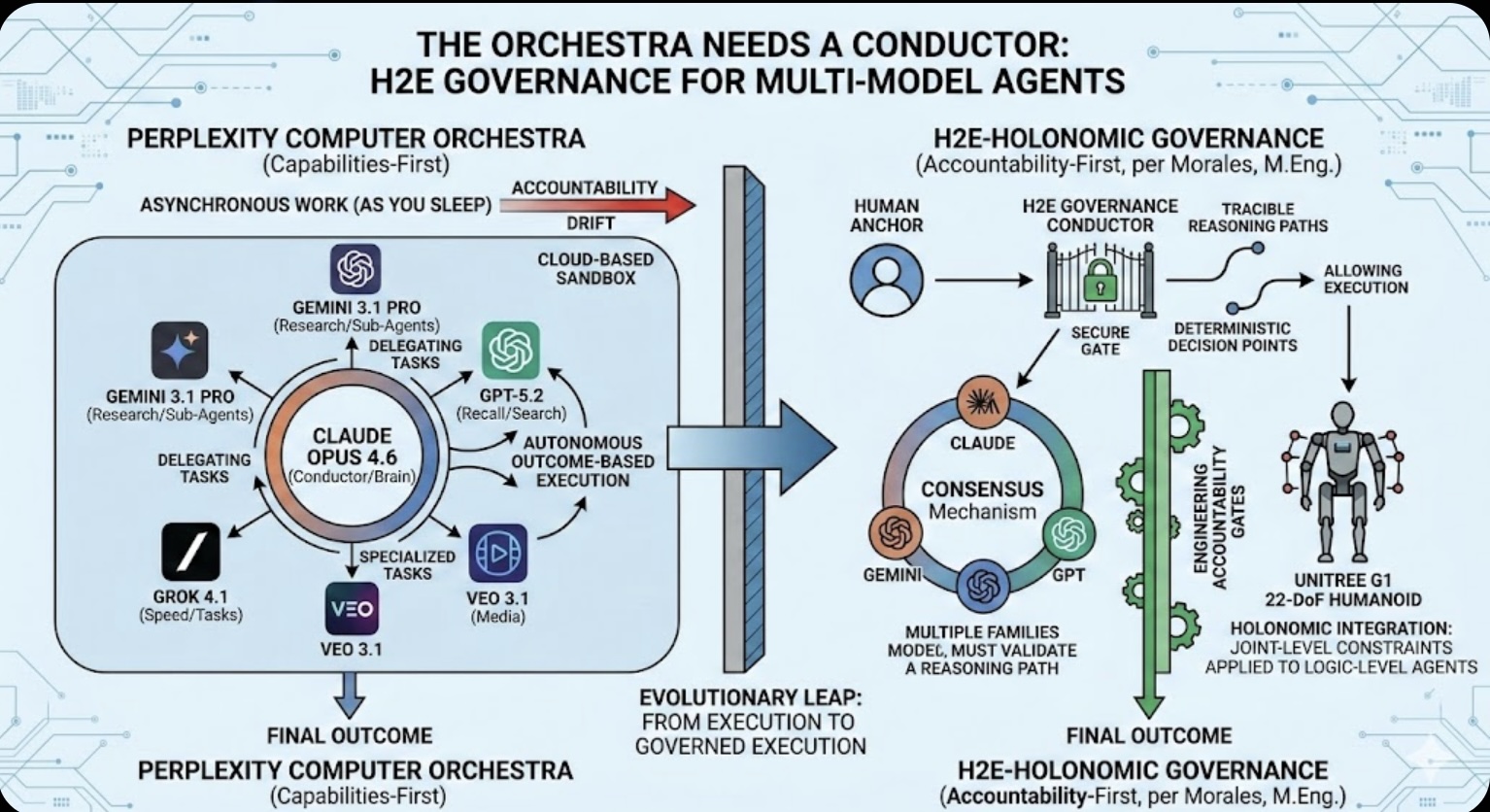 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business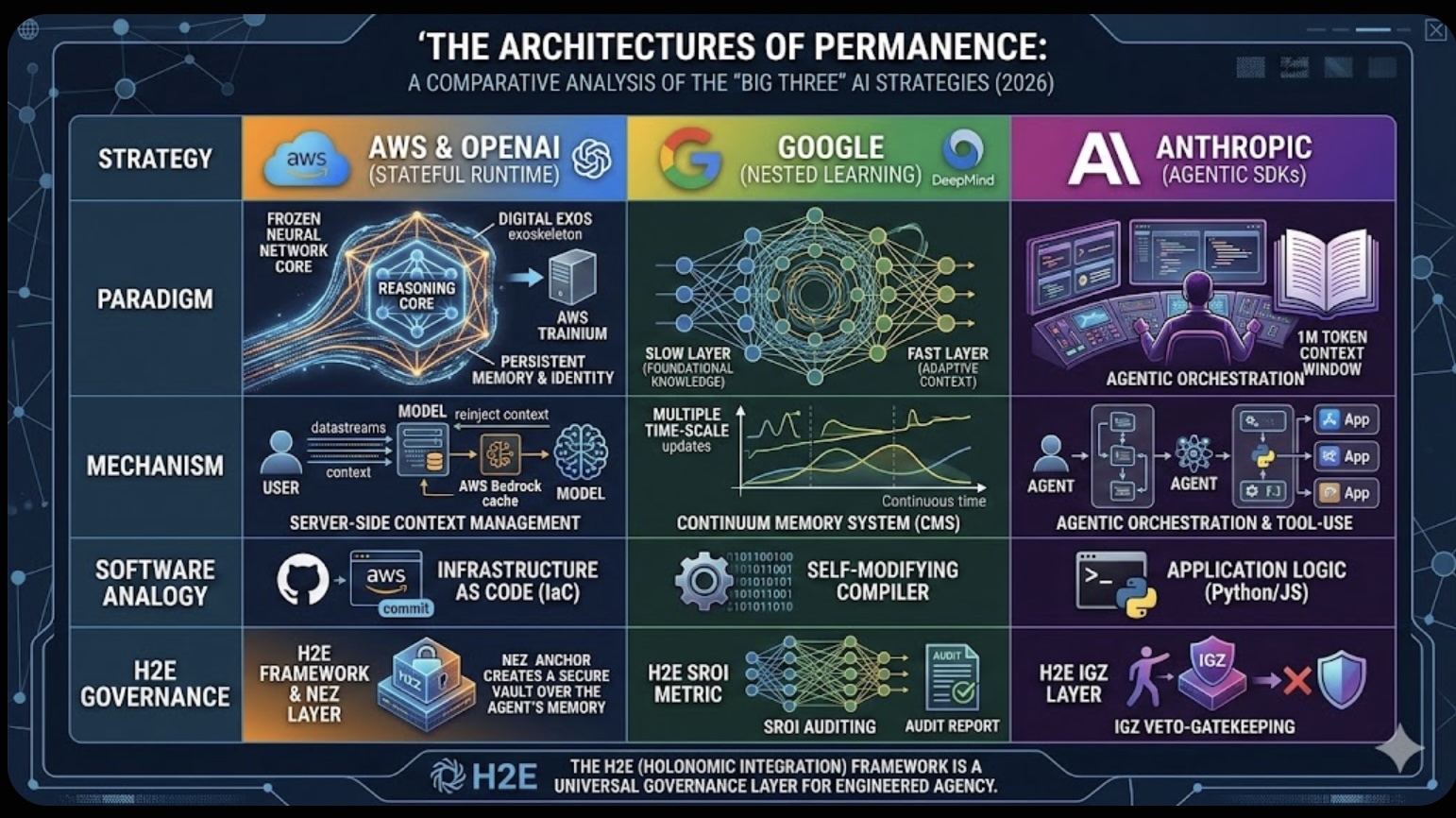 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)