Sep14

As the cybersecurity landscape continues to evolve, the challenges associated with defending
against cyber threats have grown exponentially. Threat vectors have expanded, and cyber
attackers now employ increasingly sophisticated tools and methods. Moreover, the
complexity of managing security in today's distributed hybrid/multi-cloud architecture,
heavily reliant on high-speed connectivity for both people and IoT devices, further
compounds the challenges of #cyberdefense.
One of the foremost concerns for corporate executives and boards of directors is
the demonstrable effectiveness of cybersecurity investments. However, quantifying and
justifying the appropriate level of spending remains a formidable obstacle for most enterprise
security teams. Securing additional budget allocations to bolster an already robust security
posture becomes particularly challenging in the face of a rising number of #cyberbreaches,
which have inflicted substantial reputational and financial harm on companies across diverse
industries.
The modern enterprise's IT infrastructure is an intricate web of dynamic networks,
cloud resources, an array of software applications, and a multitude of endpoint
devices. These enterprise IT ecosystems are vast and intricate, featuring a myriad of network
solutions, a diverse array of endpoint devices, and a mix of Windows and Linux servers.
Additionally, you'll find desktops and laptops running various versions of both Windows and
macOS dispersed throughout this intricate landscape. Each component within this
architecture boasts its own set of #securitycontrols, making the enterprise susceptible to
#cyberthreats due to even the slightest misconfiguration or a shift towards less secure
settings.
In this environment, a simple misconfiguration, or even a minor deviation towards less
secure configurations, can provide attackers with the foothold they need to breach an
organization's infrastructure, networks, devices, and software. It underscores the critical
importance of maintaining a vigilant and proactive approach to cybersecurity in this everevolving digital era.
As organizations look for ways to demonstrate the effectiveness of their security spend and
the policies and procedures put in place to remediate and respond to security
threats, vulnerability testing can be an important component of a security team’s
vulnerability management activities. There are several testing approaches that
organizations use as part of their vulnerability management practices. Four of the most
common are listed below:
• Penetration testing: is a common testing approach that Enterprises employ to
uncover vulnerabilities in their infrastructure. A Pen test involves highly skilled
security experts using tools and attack methods employed by actual attackers to
achieve a specific pre-defined breach objective. The pen test covers networks,
applications, and endpoint devices.
• Red Teaming: A red team performs “ethical hacking” by imitating advanced threat
actors to test an organization's cyber defenses. They employ stealthy techniques to
identify security gaps, offering valuable insights to enhance defenses. The results
from a red-teaming exercise help identify needed improvements in security controls.
• Blue Teaming: is an internal security team that actively defend against real attackers
and respond to red team activities. Blue Teams should be distinguished from standard
security teams because of the mission to provide constant and continuous cyber
defense against all forms of cyber-attacks.
• Purple Teaming: The objective of purple teams is to align red and blue team efforts.
By leveraging insights from both sides, they provide a comprehensive understanding
of cyber threats, prioritize vulnerabilities, and offer a realistic APT (Advanced
Persistent Threat) experience to improve overall security.
Although these vulnerability testing approaches are commonly used by organizations,
there are several challenges associated with them:
• These approaches are highly manual and resource intensive, which for many
organizations translates to high cost and a lack of skilled in-house resources to
perform these tests.
• The outcome of these vulnerability tests provides vital information back to the
organization to act on, they are performed infrequently due largely to the cost and
lack of skilled resources mentioned previously.
• These methods provide a point-in-time view of an organization’s security
posture which is becoming less effective for companies moving to a more dynamic
cloud-based IT architecture with an increasing diversity of endpoints and applications.
Traditional vulnerability testing approaches yield very little value because the security
landscape and enterprise IT architectures are dynamic and constantly changing.
Since testing the cybersecurity posture of organizations is becoming a top priority, it
triggered an increased demand for the latest and most comprehensive testing
solutions. Moreover, it’s almost impossible, from a practical standpoint, for multiple
enterprise security teams to manually coordinate their work and optimize configurations for
all the overlapping systems. Different teams have their own management tasks, mandates,
and security concerns. Additionally, performing constant optimizations and manual testing
imposes a heavy burden on already short-staffed security teams. This is why security teams
are turning to Breach and Attack Simulation (BAS) to mitigate constantly emerging (and
mostly self-inflicted) security weaknesses.
Definition - Breach and Attack Simulation (BAS)
Gartner defines, Breach and Attack Simulation (BAS) technologies as tools “that allow
enterprises to continually and consistently simulate the full attack cycle (including
insider threats, lateral movement and data exfiltration) against enterprise
infrastructure, using software agents, virtual machines and other means.”
BAS tools replicate real-world cyber attacker tactics, techniques, and procedures
(TTPs). They assist organizations in proactively identifying vulnerabilities, evaluating
security controls, and improving incident response readiness. By simulating these attacks in a
controlled environment, organizations gain valuable insights into security weaknesses,
enabling proactive measures to strengthen overall #cybersecurity.
BAS automates the testing of threat vectors, including external and insider threats, lateral
movement, and data exfiltration. While it complements red teaming and penetration testing,
BAS cannot entirely replace them. It validates an organization's security posture by testing its
ability to detect a range of simulated attacks using SaaS platforms, software agents, and
virtual machines.
Most BAS solutions operate seamlessly on LAN networks without disrupting critical
business operations. They produce detailed reports highlighting security gaps and prioritize
remediation efforts based on risk levels. Typical users of BAS technologies include financial
institutions, insurance companies, and various other industries.
BAS Primary Functions
Typical BAS offerings encompass much of what traditional vulnerability testing includes, it
differs in a very critical way. At a high level, BAS primary functions are as follows:
• Attack (mimic / simulate real threats)
• Visualize (clear picture of threat and exposures)
• Prioritize (assign a severity or criticality rating to exploitable vulnerabilities)
• Remediate (mitigate / address gaps
Keywords: Cybersecurity
 Why "Be Nice" Is Bad Advice
Why "Be Nice" Is Bad Advice Trust Is a Physical Phenomenon
Trust Is a Physical Phenomenon When Risk Governance Fails: The Hidden Gap Between Decisions and Accountability
When Risk Governance Fails: The Hidden Gap Between Decisions and Accountability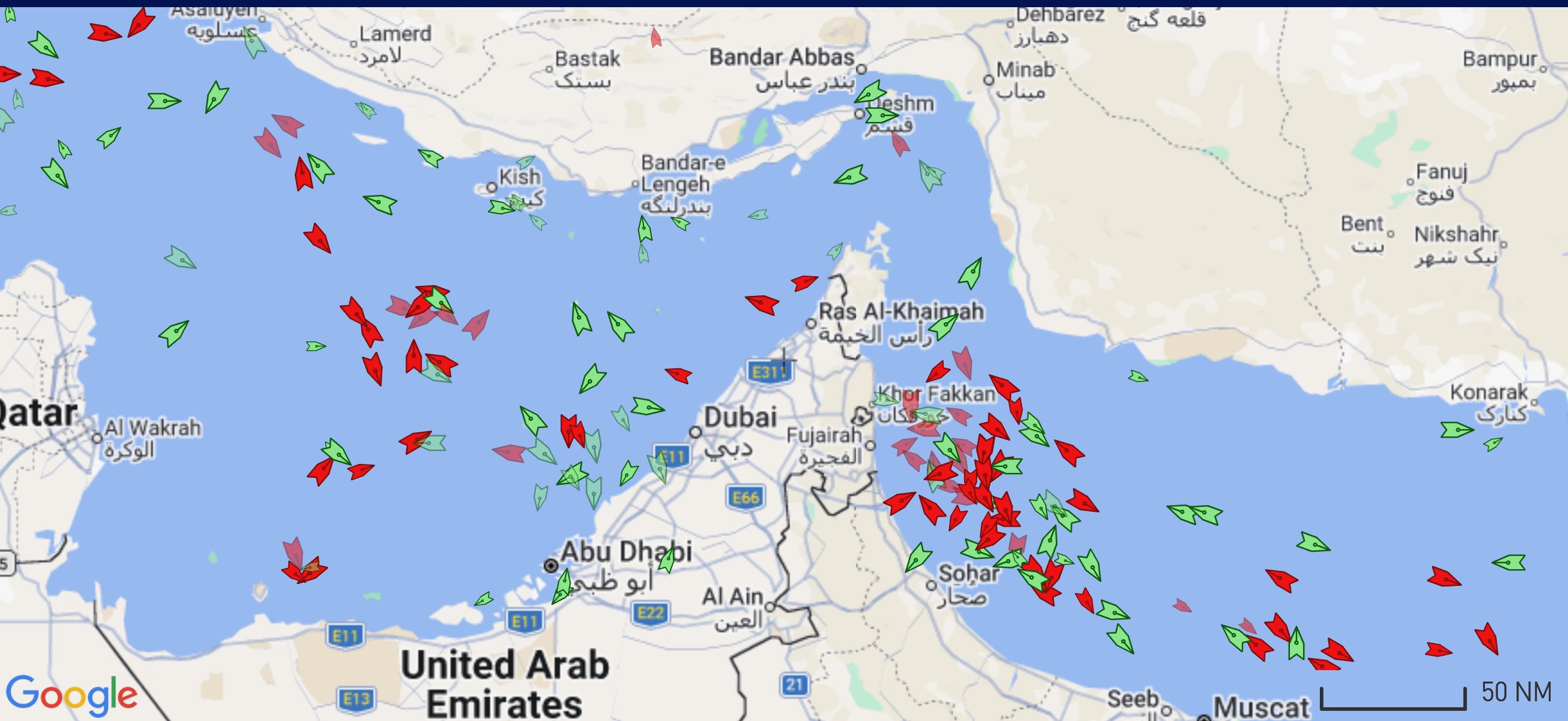 Why the Strait of Hormuz Proves Renewables Are Strategic
Why the Strait of Hormuz Proves Renewables Are Strategic Friday’s Change Reflection Quote - Leadership of Change - Change Leaders See Emerging Patterns
Friday’s Change Reflection Quote - Leadership of Change - Change Leaders See Emerging Patterns