

NAMED BY THOMSON REUTERS AS A “TOP 50 SOCIAL INFLUENCER IN RISK, COMPLIANCE.” NAMED BY IFSEC “#2 GLOBAL CYBERSECURITY INFLUENCER. TWO-TIME PRESIDENTIAL APPOINTEE. CORPORATE EXECUTIVE ROLES; GENERAL DYNAMICS, XEROX, SRA, RAPISCAN. THOUGHT LEADER, INFLUENCER, BRAND AMBASSADOR. 62k LINKEDIN FOLLOWERS, 12k TWITTER, 5k FACEBOOK. LEADERSHIP IN GOVERNMENT RELATIONS, MARKETING, BUSINESS DEVELOPMENT, AND STRATEGY
*Named Top Person To Follow on Tech by LinkedIn. Thought Leader, Influencer, Brand Ambassador.
*Adjunct Faculty at Georgetown University. Former Adjunct Faculty Johns Hopkins
* Marketing, Government Relations, Business Development, Strategic Partnerships, Corporate Growth Strategist
* Blogger and event speaker for AT&T, IBM, Blackberry/Cylance, Xerox, General Dynamics, Tripwire, others
*Received Presidential Appointments for Executive Service by two U.S. Presidents
*Helped "stand up" Office of Legislative at DHS. Served as first Director of Legislative Affairs at the DHS Science & Technology Directorate
*Served as Senior Legislative Staff (foreign affairs, security, tech) to Senator Arlen Specter, U.S. Senate
*Named Cybersecurity Marketer of the Year and Top Cybersecurity SME to Follow
* Contributor to FORBES on Technology and Cybersecurity topics
* Former Technology Partner Advisor at Bill and Melinda Gates Foundation
*EC-Council Global Advisory Board
* MIT Technology Review Advisory Panelist
* Cyber Start Up Observatory Hall of Fame
* Program Chair Quantum Security Alliance
* Judge Homeland Security Awards
* Advisory Boards (Cybersecurity, Emerging Technology, Risk Management)
* Project Management, and Marketing Certifications
* Former Auxiliary Police Officer
* Former competive powerlifter
THOUGHT LEADER, INFLUENCER, TECHNOLOGY EVANGELIST; Featured Writer/Speaker/Blogger: areas: homeland security, cyber security, CBRNE, artificial intelligence (AI), Internet of Things (IoT), science & technology, public/private partnerships, Risk Management, blockchain, innovation. Published in FORBES, Huffington Post, InformationWeek, MIT Sloan Blog, Computerworld, Federal Times, NextGov, Government Security News, Cygnus Security Media, Homeland Security Today (Visiting Editor), The Hill, Biometric Update, Bizcatalyst360, IT Security Planet, Christian Science Monitor. Published 180 + articles *
INDUSTRY EXECUTIVE: former Vice President for Homeland Security, Xerox; Former Vice President of Government Relations, SRA; Former Vice President R&D Rapiscan
* Co-leader of two top Homeland Security Groups on LinkedIn. Run 15 other business, tech LI groups
Available For: Authoring, Consulting, Influencing, Speaking
Travels From: Washington,DC
| Chuck Brooks | Points |
|---|---|
| Academic | 55 |
| Author | 456 |
| Influencer | 976 |
| Speaker | 51 |
| Entrepreneur | 25 |
| Total | 1563 |
Points based upon Thinkers360 patent-pending algorithm.
 Selected Chair of Quantum Impacts on the Internet of Things by the Quantum Security Alliance
Selected Chair of Quantum Impacts on the Internet of Things by the Quantum Security Alliance
Tags: IoT, Management, Leadership
 Disruptive Tech & Org Change
Disruptive Tech & Org Change
Tags: Cybersecurity, Digital Disruption, Innovation
 How Intel Core Ultra Processors and Intel vPro Can Help Keep Your PC Secure
How Intel Core Ultra Processors and Intel vPro Can Help Keep Your PC Secure
Tags: Cybersecurity, Emerging Technology, Security
 Cyber-Securing Space Systems A Growing Global Concern
Cyber-Securing Space Systems A Growing Global Concern
Tags: Cybersecurity, Emerging Technology, Security
 Healthcare Cybersecurity: A Global Imperative
Healthcare Cybersecurity: A Global Imperative
Tags: Cybersecurity, Emerging Technology, Security
 Artificial Intelligence and the Growing Importance of Chief Digital Officers
Artificial Intelligence and the Growing Importance of Chief Digital Officers
Tags: Cybersecurity, Emerging Technology, Security
 The Target Breach 10 Years Later
The Target Breach 10 Years Later
Tags: Cybersecurity, Emerging Technology, Security
 Grey Swans on the Horizon; AI, Cyber, Pandemics, and ET Scenarios
Grey Swans on the Horizon; AI, Cyber, Pandemics, and ET Scenarios
Tags: AI, Cybersecurity, Emerging Technology, Security
 2024 enterprise cybersecurity forecasts
2024 enterprise cybersecurity forecasts
Tags: Cybersecurity, Security
 Computational Capabilities That Will Transform the World
Computational Capabilities That Will Transform the World
Tags: AI, Cybersecurity, Emerging Technology
 Cybersecurity Awareness: Data Protection & Incident Response Strategies
Cybersecurity Awareness: Data Protection & Incident Response Strategies
Tags: Cybersecurity, Risk Management, Security
 Cybersecurity Awareness: Risk Management, Malware and Phishing Strategies
Cybersecurity Awareness: Risk Management, Malware and Phishing Strategies
Tags: Cybersecurity, Risk Management
 Spooky Cyber Statistics And Trends You Need To Know
Spooky Cyber Statistics And Trends You Need To Know
Tags: Cybersecurity, Risk Management, Security
 A Primer On Artificial Intelligence And Cybersecurity
A Primer On Artificial Intelligence And Cybersecurity
Tags: AI, Cybersecurity, Emerging Technology
 GovCon: Topics in Cybersecurity, Emerging Tech and Strategy & Policy
GovCon: Topics in Cybersecurity, Emerging Tech and Strategy & Policy
Tags: Cybersecurity, Emerging Technology
 Artificial Intelligence: Transforming Healthcare, Cybersecurity, and Communications
Artificial Intelligence: Transforming Healthcare, Cybersecurity, and Communications
Tags: AI, Cybersecurity, Emerging Technology
 Thoughts on Trends in Cybersecurity, Tech, and Innovation -- Recent Interviews of Chuck Brooks
Thoughts on Trends in Cybersecurity, Tech, and Innovation -- Recent Interviews of Chuck Brooks
Tags: Cybersecurity, Risk Management, Security
 Academia, Industry, And Government Can Create Innovative Partnerships And Help Secure Our Digital Future
Academia, Industry, And Government Can Create Innovative Partnerships And Help Secure Our Digital Future
Tags: AI, Cybersecurity, Innovation
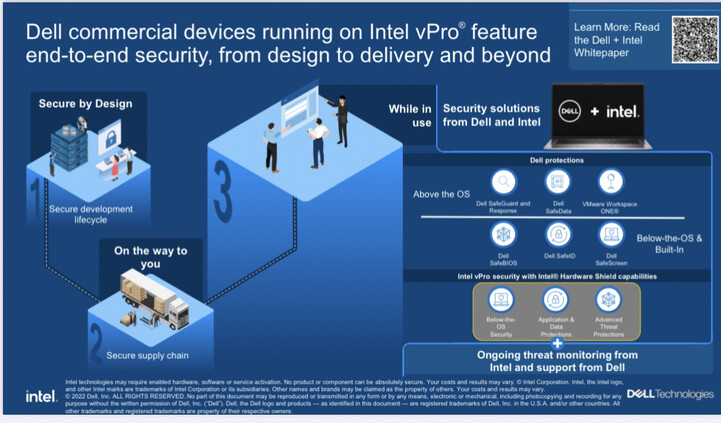 My Dell Laptop Powered By Intel vPro Offers End To End Built-In Protection Against Advanced Cyber-Threats (Including AI)
My Dell Laptop Powered By Intel vPro Offers End To End Built-In Protection Against Advanced Cyber-Threats (Including AI)
Tags: Cybersecurity, Risk Management, Security
 SOCS And Corporate Cybersecurity Hubs Growing In Importance and Capabilities In New Threat Landscape
SOCS And Corporate Cybersecurity Hubs Growing In Importance and Capabilities In New Threat Landscape
Tags: Cybersecurity
 Cybersecurity Trends & Statistics For 2023; What You Need To Know
Cybersecurity Trends & Statistics For 2023; What You Need To Know
Tags: AI, Cybersecurity, Innovation
 Quantum Tech Needed To Secure Critical Data From Quantum Decryption
Quantum Tech Needed To Secure Critical Data From Quantum Decryption
Tags: AI, Cybersecurity, Quantum Computing
 4 Mind-Boggling Technology Advances In Store For 2023
4 Mind-Boggling Technology Advances In Store For 2023
Tags: AI, Cybersecurity
 Cybersecurity and Business Computing Performance -- Out of the Box for 2023!
Cybersecurity and Business Computing Performance -- Out of the Box for 2023!
Tags: Cybersecurity, Security, National Security
 A Cybersecurity Primer for The C-Suite, SMBS, and Organizations
A Cybersecurity Primer for The C-Suite, SMBS, and Organizations
Tags: Cybersecurity, Risk Management, Security, National Security
 For Cybersecurity Awareness Month (and Halloween) – Some Scary Cyber Threat Stats
For Cybersecurity Awareness Month (and Halloween) – Some Scary Cyber Threat Stats
Tags: Cybersecurity, Risk Management, Security, National Security
 The Search For Extraterrestrial Life, UFOS, And Our Future
The Search For Extraterrestrial Life, UFOS, And Our Future
Tags: AI, Emerging Technology
 Cybersecurity of Space Systems
Cybersecurity of Space Systems
Tags: Cybersecurity, Emerging Technology, Security
 Tech and Cyber Predictions For 2024
Tech and Cyber Predictions For 2024
Tags: Cybersecurity, Emerging Technology, Security
 Risk Management of the Emerging Tech and Security Landscapes for 2024
Risk Management of the Emerging Tech and Security Landscapes for 2024
Tags: Cybersecurity, Emerging Technology
 Cybersecurity Tips For The Holiday Shopping Season
Cybersecurity Tips For The Holiday Shopping Season
Tags: Cybersecurity, Emerging Technology
 Designed and teaching course at Georgetown on Disruptive Technologies
Designed and teaching course at Georgetown on Disruptive Technologies
Tags: Cybersecurity, Risk Management, Security
 Brooks Consulting International
Brooks Consulting International
Tags: Cybersecurity, Emerging Technology, Risk Management
 Thinkers 360 Thought Leader Chuck Brooks selected as a finalist for the Top 50 Marketer Award.
Thinkers 360 Thought Leader Chuck Brooks selected as a finalist for the Top 50 Marketer Award.
Tags: Innovation, GovTech, Marketing, Security
 10 cybersecurity experts to follow on social media
10 cybersecurity experts to follow on social media
Tags: Cybersecurity, Emerging Technology, Security
 Top 30 Cybersecurity Experts You Should Follow In 2021
Top 30 Cybersecurity Experts You Should Follow In 2021
Tags: Cybersecurity, Leadership, Security
 Strategic Paths to Cybersecurity
Strategic Paths to Cybersecurity
Tags: Cybersecurity, Security, National Security
 Cyber Startup Observatory -- Interview with Chuck Brooks
Cyber Startup Observatory -- Interview with Chuck Brooks
Tags: Cybersecurity, GovTech, International Relations
 The Urgency of Protecting Critical Infrastructure from both digital and physical threats
The Urgency of Protecting Critical Infrastructure from both digital and physical threats
Tags: Cybersecurity, Leadership, Security
 Real World Intelligence and Global Cybersecurity Threats
Real World Intelligence and Global Cybersecurity Threats
Tags: Cybersecurity, Management, Security
 Cybersecurity after COVID19
Cybersecurity after COVID19
Tags: Cybersecurity, Emerging Technology, Security
 Accelerating Innovation, Security, & Education in the Digital Age August 24, 2023
Accelerating Innovation, Security, & Education in the Digital Age August 24, 2023
Tags: Cybersecurity, Emerging Technology, Security
 Why Is Cybersecurity at a Crossroads?
Why Is Cybersecurity at a Crossroads?
Tags: Cybersecurity, Risk Management, Security
 Renew cyber hygiene strategies for 2022
Renew cyber hygiene strategies for 2022
Tags: AI, Cybersecurity, Security
 Chuck Brooks - Cyber Insights for 2021
Chuck Brooks - Cyber Insights for 2021
Tags: Cloud, Cybersecurity, Leadership
 Chuck Brooks: Security by Design Needed to Safeguard Energy Infrastructure From Cyber Attacks
Chuck Brooks: Security by Design Needed to Safeguard Energy Infrastructure From Cyber Attacks
Tags: Cybersecurity, Emerging Technology, Risk Management, Security
Tags: AI, Cybersecurity, Marketing
 Thought Leader and Influencer Interview with Chuck Brooks, President, Brooks Consulting International and Adjunct Faculty Georgetown University
Thought Leader and Influencer Interview with Chuck Brooks, President, Brooks Consulting International and Adjunct Faculty Georgetown University
Tags: Cybersecurity, Digital Transformation, Marketing
Tags: COVID19, Cybersecurity, Emerging Technology
Tags: Cybersecurity, GovTech, Business Strategy

Tags: Cybersecurity, Emerging Technology, Risk Management
 YOURSELF READY for the DIGITAL ERA … 5th INDUSTRIAL REVOLUTION Interview of Chuck Brook
YOURSELF READY for the DIGITAL ERA … 5th INDUSTRIAL REVOLUTION Interview of Chuck Brook
Tags: AI, Emerging Technology, Security

Tags: Cybersecurity, Emerging Technology, Risk Management
Tags: Cybersecurity, Emerging Technology, Risk Management
 The IFSEC 2 Global Cyber Security Influencer for 2018
The IFSEC 2 Global Cyber Security Influencer for 2018
Tags: Cybersecurity, Risk Management, Security

Tags: Cybersecurity, Emerging Technology, Risk Management
Tags: Cybersecurity, Emerging Technology, International Relations
Tags: Cybersecurity, Innovation
 Balancing security + gov cloud innovation
Balancing security + gov cloud innovation
Tags: Cloud, Cybersecurity, Innovation
 Industry 4.0 and Cybersecurity 2.0 –- Opportunities & Challenges -- IIoT World Days.
Industry 4.0 and Cybersecurity 2.0 –- Opportunities & Challenges -- IIoT World Days.
Tags: Cybersecurity, IoT, Risk Management
 TIC Consortium Panel: Emerging Tech for Hybrid Warfare
TIC Consortium Panel: Emerging Tech for Hybrid Warfare
Tags: Cybersecurity, Emerging Technology
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity, Education
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity
Tags: Cybersecurity, Emerging Technology, Security
 Seyfarth and NY Metro InfraGard Present: Lunch with America’s Cybersecurity Influencers
Seyfarth and NY Metro InfraGard Present: Lunch with America’s Cybersecurity Influencers
Tags: Cybersecurity, Management, Leadership
 RaCE: Resilience and Collaboration Extended
RaCE: Resilience and Collaboration Extended
Tags: Cloud, Cybersecurity, Digital Transformation
 2020 Cyber Innovators Summit
2020 Cyber Innovators Summit
Tags: Cybersecurity, Management, Leadership
 October Cyber Bytes Networking Event: Election Security
October Cyber Bytes Networking Event: Election Security
Tags: Cybersecurity, Management, Leadership
 CISO's View: Emerging Technologies Impacting the IAM Landscape
CISO's View: Emerging Technologies Impacting the IAM Landscape
Tags: Cybersecurity, Emerging Technology, GovTech, Risk Management
 Social Media Platforms Are Helping Shape Business Success
Social Media Platforms Are Helping Shape Business Success
Social media has transformed the way people interact and conduct business both in the public and private sector. The Covid19 pandemic, combined economic factors, have led to the emergence of remote work and hybrid environments and different ways of doing commerce. The move away from business lunches, live events, and meetings has propelled digital platforms into becoming a main fulcrum for communications and branding. Those social platforms have especially impacted components of business development, sales, government relations, and marketing and are helping shape pathways to success.
Many users enjoy social mediums because they control the content, and it is non-invasive. Also, it can be perpetually shared. Social media has become a platform to communicate who we are and what we do. Platforms such as LinkedIn, Twitter, and Instagram, have now become a daily means for sharing content, building networks, and reaching targeted markets. Thought leadership on meaningful topics is of timely interest to everyone and the use of subject matter experts and influencers have become a primary means for brand amplification via articles, blogs, podcasts, and online events.
Today, most senior-level executives on both the public and private sectors have LinkedIn profiles, including administrators, CEOs, CTO, CIOS and their numbers are increasing. They often use it as a conduit for 1) Branding 2) Socializing/Networking; 2) Basic Intelligence; 3) Events: and 4) Strategic Partnering/Marketing.
Branding: the trend of digital brand amplification began to grow at the beginning of the outset of the pandemic. Because of the lack of in person meetings, many companies, new & old, large & small, sought to be more visible and recognized for the unique viability for branding on social media platforms. Companies were and are seeking quality and interesting content that helps enable them to be able to connect with peers and clients. A benefit of social media digital marketing and brand amplification is that it can be very cost-effective, repetitive, and can generate revenue and build positive reputations. A good written message, video or graphic can have a long shelf-life and be shared widely across various social media platforms. Influencers have also become part of the branding mix; expertise bring credibility and attention and many companies have expanded strategies that use influencers and thought leaders who can augment company marketing and sales.
Socializing/networking: social media is in its essence “social.” It is an outlet for networking and connecting with people who share your interests, goals, and professional paths. A platform like LinkedIn, Facebook, Instagram, and Twitter are useful for reconnecting to people you have worked with in past jobs, friends, and alumni of universities, and colleges. In particular, the service encourages you to join professional and hobby interest groups where you can post articles and engage in discussion with group members. I am a big proponent of LinkedIn for networking where I have over 73,000 followers, especially with targeted groups. For example, I have management roles in several of the largest and most influential homeland security groups on LinkedIn. Another key area of group ownership and involvement for me on LinkedIn is with cybersecurity and emerging technology groups where I find the readership are exceptionally informed and active. Also, as a “foodie”, I created the “DC Foodies” LinkedIn group to reach out to others in the greater Washington, DC area that may have a passion for food, wine, and restaurants. On LinkedIn there is a group for almost every subject from healthcare, governing, martial arts, Space, to quantum physics.
Basic Intelligence: Another function of social media is that it provides you with working biographies of members. Whenever I have a meeting with someone new, I can usually find their profile on LinkedIn and see where they worked, what schools they attended and who we know in common. Also, by following the posts in groups, I can view the latest news from a variety of sources on a topic of interest. Also, almost all federal agencies and public entities have their own profiles (and often groups) on LinkedIn that make the basic intel process quick and easy.
Events: There is no better place to go to find out who is hosting what than on social media. This includes LinkedIn, Twitter, Instagram, Facebook in the event domain. Since most publications are intertwined between print and digital media, social media outlets are a fulcrum for seeing what activities are happening in personal or business areas of interest daily.
Strategic Partnering/Marketing: social media is really the Holy Grail for strategic partnering and marketing. Messaging is immediate, perpetual, and cost-effective. It is also much targeted and will allow you to focus communications to audiences, both individual and groups that may have an interest in your offerings and services. For those who are specifically focused on the federal market, LinkedIn is an especially good resource for finding teaming members and potentially partners to pursue opportunities. By being active on LinkedIn, companies can often find you and reach out for help in areas that may be mutually beneficial. As government encourages diverse and multiple partners to work together on programs, the importance of having a strong stable of networked partners is becoming more of a premium.
We are still only in the early era of social media. It will continue to grow and be fused into all aspects of our lives, especially with the growth of augmented reality and emerging communication technologies. Social media vehicles like LinkedIn already have great utility in the workplace both in the corporate world and in government. Linked and other social media platforms are already shaping communications. “Linking in” and being active on social media platforms have become more of an imperative than a choice for those who want to thrive in a digital world.
Chuck Brooks, President of Brooks Consulting International, and Adjunct Faculty at Georgetown University, is a Technology Evangelist, Corporate Executive, Speaker, Writer, Government Relations, Business Development, and Marketing Executive. LinkedIn named Chuck as one of “The Top 5 Tech People to Follow on LinkedIn.” He was named as one of the world’s “10 Best Cyber Security and Technology Experts” by Best Rated, as a “Top 50 Global Influencer in Risk, Compliance,” by Thomson Reuters, “Best of The Word in Security” by CISO Platform, and by IFSEC as the “#2 Global Cybersecurity Influencer.” He was also named “Best in The World in Security” by CISO Platform, one of the “Top 5 Executives to Follow on Cybersecurity” by Executive Mosaic, and as a “Top Leader in Cybersecurity and Emerging Technologies” by Thinkers360. Chuck was named by Oncon in 2019 “Top Global Top 50 Marketer” by his peers across industry.
Chuck also a Cybersecurity Expert for “The Network” at the Washington Post, Visiting Editor at Homeland Security Today, Expert for Executive Mosaic/GovCon, and a Contributor to FORBES. He is a featured contributor to Thinkers360
Tags: Social, Marketing, Business Strategy
 “Innovation Foraging” on Social Digital Mediums
“Innovation Foraging” on Social Digital Mediums
In the science, technology worlds, there is a category referred to as “technology foraging,” or the searching for smart ideas and emerging technologies that may exist already in research institutions of found in patents to fill gaps and offer new solutions. Technology foraging has been an engine for the technological transformation now taking place in society. It has served as a catalyst for discoveries of many products brought to the marketplace.
The foraging process is often conducted in research centers by national labs, universities, and in government & corporate innovation hubs. It has expanded commensurately with the rapid pace of innovation in our new era of exponential digital transformation where humans and computing devices are intertwined, and data is more accessible. Please see my article Technology Foraging for Cybersecurity Solutions Technology Foraging for Cybersecurity Solutions | AT&T Cybersecurity (att.com)
Digital transformation combined with tech foraging of the 4th Industrial Era has led to significant jumps in innovation of technologies. This includes, for example, emerging tech such as big data, artificial intelligence, IoT, smart cities, 5G wireless, virtual & augmented reality, nanotechnologies, robotics, self-driving cars, 3-D Printing, cybersecurity, quantum computing, predictive data analytics, Biometrics and wearables, self-healing materials, bioinformatics, genetic engineering, and a new world of medical applications.
The digital transformation It has also impacted communication mediums, especially social media where research, ideas, analyses, and opinions are cultivated by open sharing and interaction. The networking and information sharing on digital mediums can be viewed as a foraging process. The pace of digital expansion and change is happening so rapidly that it can be quite overwhelming just to try to keep up. But social media does offer a pathway to do so via innovation foraging and collaborative information sharing.
For example, my career passion revolves around searching and reading about topics in cybersecurity. Using social media, I can keep abreast of the latest news and events. A case in point is the recent Colonial Pipeline breach. Almost immediately after happened, detailed descriptions of the breach and surrounding issues such as ransomware were posted on LinkedIn, Twitter, and other digital mediums. There was a potpourri of expert perspectives available, including posts on technical analyses, and posts on geopolitical and economic implications. Forging through posts you can also develop your own knowledge to explore remedies and policy frameworks that may apply digital impact to your own professional or business circumstances.
From my perspective as cyber security & technology strategist, the extensive resources of LinkedIn combined with their supporting analytics provides a great platform to communicate, educate and promote. For me, LinkedIn groups, including the dozen groups I created, serve as the most optimal social media digital offerings for foraging. Research on LinkedIn is significantly amplified by the myriad of specialized information security LinkedIn groups that I can pull insightful and timely data from on a regular basis.
Several years back I wrote an article for LinkedIn called Why LinkedIn is an Indispensable Medium for Security Professionals Why LinkedIn is an Indispensable Medium for Security Professionals | LinkedIn Marketing Blog In that blog I noted that” LinkedIn has become part of the fabric of how I (and a majority of my peers) communicate, operate, and conduct business. For me, LinkedIn groups serve as interactive, informative forums. Many of the members in my groups are security professionals who have important roles in government or industry, including CISOS, CIOs, CTOs, or members of the C-Suite who possess deep subject matter knowledge.” I also stated that for thought leadership on homeland security and cybersecurity issues, that “LinkedIn is a real force for digital influence. It is an effective platform for educating, evangelizing, and promoting discussion of the cutting risk management issues.”
The value of LinkedIn for evangelism and marketing goes far beyond immediate connections. The extensive resources of LinkedIn combined with the intrinsic marketing capabilities based upon intelligence analytics provides a ready platform to communicate, educate and promote. In my major areas of interest, cybersecurity and emerging tech, I am very active in interchange of news and innovative ideas with groups, and also with my 70,000 direct follower connections. It facilitates keeping up with cybersecurity and emerging technology trends that I can share with others across digital media.
With 18 years under its belt and a membership globally of over 800,000 users, LinkedIn has become increasingly valuable as a forging resource and influence platform for branding people and companies. Twitter offers good avenues for networking, and often is starting point for interesting links that spur more foraging on other media sites. Both platforms offer users measurable metrics to track effectiveness of content and interactions.
For employees at a company or organization, foraging (and info sharing) on digital mediums as a corporate strategy can help drive collaboration between often aloof silos comprised of the c-suite, marketing, legal, and sales. A social media platform can also foster company awareness & relationship, cultivate business networks, and can even be used as a research tool for due diligence. For both companies and individuals, social digital platforms can serve as a resource and enabler for innovation by sharing important data derived from foraging among informative posts.
Chuck Brooks, President of Brooks Consulting International, is a globally recognized thought leader and subject matter expert Cybersecurity and Emerging Technologies. LinkedIn named Chuck as one of “The Top 5 Tech People to Follow on LinkedIn.” He was named by Thompson Reuters as a “Top 50 Global Influencer in Risk, Compliance,” and by IFSEC as the “#2 Global Cybersecurity Influencer.” He was featured in the 2020 Onalytica "Who's Who in Cybersecurity" – as one of the top Influencers for cybersecurity issues. He was also named one of the Top 5 Executives to Follow on Cybersecurity by Executive Mosaic. He is also a Cybersecurity Expert for “The Network” at the Washington Post, Visiting Editor at Homeland Security Today, Expert for Executive Mosaic/GovCon, and a Contributor to FORBES.
Chuck Brooks LinkedIn Profile: https://www.linkedin.com/in/chuckbrooks/
Chuck Brooks on Twitter: @ChuckDBrooks
Tags: Cybersecurity, Digital Transformation, Innovation
 Brooks Consulting International
Brooks Consulting International
Location: Washington, DC Date Available: September 30th, 2020 Fees: Negotiable
Submission Date: September 29th, 2020 Service Type: Service Offered
 How Intel Core Ultra Processors and Intel vPro Can Help Keep Your PC Secure
How Intel Core Ultra Processors and Intel vPro Can Help Keep Your PC Secure Cyber-Securing Space Systems A Growing Global Concern
Cyber-Securing Space Systems A Growing Global Concern Healthcare Cybersecurity: A Global Imperative
Healthcare Cybersecurity: A Global Imperative Brooks Consulting International
Brooks Consulting International