As the recrimination and fingers pointing continues, the theatre surrounding the Solarwinds hack shows why we need to move beyond Passwords. Yes you heard it here - Passwords, are the problem.
Are we really surprised these types of hacks take place? The average hack remains undetected for 220 days or more… I will also postulate those intent on stealing your information assets are already on the inside, - the sleeping enemy within.
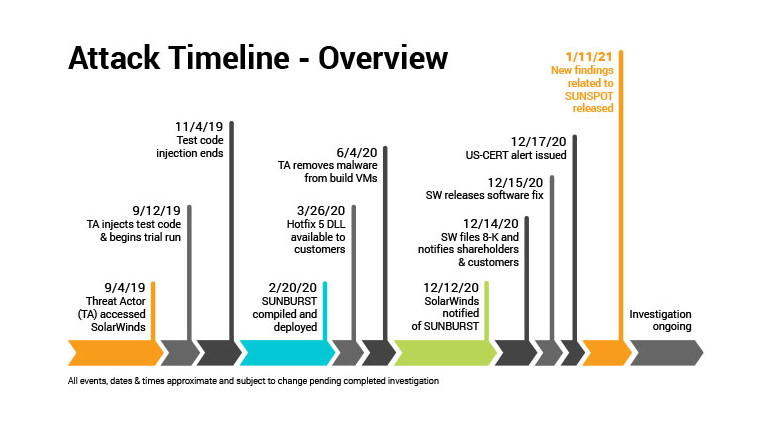
Whilst the precise details of the SolarWinds attack may never be know it is clear a catastrophic event happened. A critical collapse at every level of security. Or was it? Given the lessons from Sandworm attacks on US national infrastructure were themselves simple in approach and execution. Create a beachhead, a cascade strategy - get further inside, hide, gather and distribute, then spread the infectious malware far and wide, and keep repeating.
It is always interesting to me to witness how large businesses, government agencies and national infrastructure work with cyber security firms. In this case the compromise ( a sunburst) was directed against the Orion development environment, highlights the sheer scale of the vulnerability, and how inadequate any cyber security systems really is.
Will the Solarwinds attack become the new poster boy for the hacking community, whether state sponsored or frustrated opportunist given the amount of mayhem that it created? How sophisticated was the SolarWinds attack? Not very, but it was genius thinking. They way in, a compromised User Account - Password, created a small gap through which a malware was injected. The new patch on a development system distributed to all users and systems to make things more secure, was the issue. Compromising a software update, the Cyber Security software was going to deploy. The perfect crime - the defenders unknowingly compromising their own systems! Don’t you just love it.
Every hacker is wishing they thought of it - injecting malware into a trusted SolarWinds software update, the hackers were able to remain undetected, across the entire user network for months and months without detection. We may never know how long they were on the inside.
Once on the inside the hackers compromised and collected all users identity access rights, secure tokens to keep unlocking systems, even the heavily encrypted ones. I bet the hackers couldn’t believe their luck. A simple intrusion strategy that manifested in seeing and knowing everything. Happy days!
The way in? Point of least resistance - human frailties, mistakes, stupidity and cross use of apps, mixing social and business activities from a single device, moving from one to another while keeping everything logged in. Or was it the generic password sent with the Orion update, or was it as part of an automated software update, where Admin Rights handled global decision making? Or was it a case of get inside, find the server or user areas that hold all of the passwords, an old ploy.
The strategy was clearly those of a rogue state, given the size of the opportunity an ‘update server’ that supports thousands of high-security organisations that in this instance included the US Departments of Defence, Homeland Security and other core functions - all at once.
The question remains do cyber security companies ‘eat their own dog food’ and would we know? We can be sure based on similar hacks, the developer or engineer preparing the distribution of the ‘patch’ to gain access to the Orion update server was likely to be ‘SolarWinds123’? Maybe not? I would still have a small wager on this one…
The common theme - 90% of hacks use old fashioned Passwords. The root cause of most security issues and the people Passwords are attached to, especially now we have 90% of the people outside the company infrastructure working from home. Indeed the SolarWinds’ CEO confirmed ‘the Office 365 environment was the likely first breach, to gain access to employee email accounts opening the door wide open to the Orion systems development server, from which new code could be distributed unchallenged’.
Eventually the CEO Sudhakar Ramakrishna mentioned in a blog “We’ve confirmed that a SolarWinds email account was compromised and used to programmatically access accounts of targeted SolarWinds personnel in business and technical roles,” he continues “By compromising credentials of SolarWinds employees, the threat actors were able to gain access to and exploit our Orion development environment.” Attack the bodyguard, of the bodyguard…
What has made the Solarwinds hack more interesting, it emerged hackers were covering their attacks, in a sense walking back over their steps, removing fingerprints and deleting any evidence they were there (in the system) at all. All this without the use of Quantum AI systems?
The next evolution of threat is shapeshifting code, that hides. If detected copies itself, moves, destroys itself, or fragments. All this one did was disguise itself as one of the good guys, piggybacking on the good guys system. A free pass.
Could this hack have been prevented? One of my cients is a leader in Post-Quantum Encryption, a business called PostQuantum Ltd who work with encryption that even the most powerful Quantum Machines cannot breech. There are no excuses. The technology exists to defend against these threats.
The Post-Quantum Ltd company develops open source algorithms for quantum-safe public key encryption, not only removing the primary quantum threat but also securing what we have today. A simple relatively inexpensive overlay. The second level ‘braces’, the one that really holds your trousers up, not the belt for show, that keeps things neat a tidy and stops the ugly bits leaking.
The bad actors is not just the hacker, but also the use of Passwords themselves, as Users become bad actors, part of the crime due to laziness, stupidity and ignorance. Passwords are a poor 20th century concept that implicates everyone and makes everyone a target. As soon as a single password or a single user is compromised, the entire infrastructure is deemed open, vulnerable, and every security system rendered worthless.
Two things are important. Validating who or what is at each end of the network, and the content being sent has trusted data/information that hasn’t already been infected. The team at Post-Quantum Ltd insist in order to defend the enterprise the identity has to be confirmed biometrically, a PASSWORDLESS envrionment. Quick, secure biometric checks for logging in to all applications, delivered as a cloud or in-house ‘on-prem’ service. Eliminating the primary vulnerability the person and the password - stolen credentials, the source of circa 80% of hacks today.
Even with 2FA (two factor authentication in place), a breached Office 365 email account may still have allowed an attacker to gain entry with the users phone or message services (IMessage) going visibility of the 2FA code sent to the device, as the issue remains - Who is it? The addition of the Second Factor is no longer enough. The Post-Quantum team mention again the only way for authentication to work is when access credentials are tied biometrically to the individual, and doesnt become a best kept shared secret existing in more than one place like a password, pin code or record of a fingerprint scan that are transferable.
Identifying who is in your network beyond reasonable doubt, man and/or machine. Then validate what exactly is being sent down the pipe, across the network. The Solarwinds hacks demonstrates the new security patch was probably already infected. Unfortunately biometrics has had a ‘bad wrap’ - solutions can be expensive and also tied to a validation point centrally or on each device, as biometric files can be large, making them harder to work with and not able to be sent efficiently, maybe unless ‘hashed’ to a secure Blockchain, using a zero trust protocol.
How to validate Who, having seen the recent Tom Cruise Deep Fake messages going around, true authentication is often dependent on independent corroborative checking. But it gets worse as all trust evaporates as soon as a users mobile phone is compromised, lost or stolen. This is because the hackers toolkit makes it easy for them to re-trace fingerprints, facial recognition (re-facing to replace or bypass the user) from what is already stored on the device. The Founder at Post-Quantum - Andersen Chang confirms the right solution solves issues using a biometric check from a trusted third party, a form of multi-party consensus, enabling the user to login from any device and location they choose.
Each device has an identity - IAM and with passwords and even face recognition seemingly validating Who is it really remains a grey area. From an enterprise or large organisation (government) perspective there is no appetite to replace the current infrastructure, as lots of people who have signed off big expenditure will have ‘egg on face’, instead it is possible to add the ‘braces’ (new layer), a set of standards like OpenID Connect already exists.
Replacing SolarWinds password with a simple facial scan, combined with ‘three line voice’ check, before they could access the Orion system, but mostly before the firm’s employees accessed its Microsoft 365 environment. Whilst one can always speculate after the event, a take a superior position of - ‘if only’ there is a strong case that suggests eliminating Passwords and replace this with password less biometric validation would have most likely prevented the breech. We now have to move beyond static and transferable credentials for authentication and non-repudiation, the infamous Password, that hackers take great pleasure, similar to the team at Bletchley Park, solving the puzzle .
However we can take this even further for mission critical “cannot fail” infrastructure such as defence, critical national infrastructure and core capital markets infrastructure. In this scenario the authentication, the key is a segregation of duties that control parts of the biometric and device landscape. Separating access rights, from entry rights, from supervisors and admin rights. A rogue nation state may still have the resources and capabilities to compromise even this, but unlikely.
The obvious solution - a cryptographically based multi-party approval would be ideal as in the SolarWinds case, where above all else a critical update (software patch) cannot leave the sender, the source - unless a quorum of supervisors and permission have been released. Whilst these may seem unnecessary, as they say in Aliens when they decide to take off and new the Aliens that have assumed control of the facility from space “Its the only way to be sure”!
Author: Nick Ayton
Copyright 2021
BIO
Nick Ayton is a leading deep technology influencer and thought leader who operates at the forefront of AI, Blockchain, Quantum Computing and is involved in projects that include Quantum Photonic Silicon Processing, real time 3D rendering, Post Quantum Cryptography... A sought after speaker and strategist, he founded Chainstarter Ventures that helps entrepreneurs capital from Family Offices. The business focuses on the middle east and assists with capital raising, business development and market entry. Having spent 45 years in technology, founded several tech startup he is a prolific writer and is making a TV Series that is set against the backdrop ion the existential risk of AI and race for supremacy between Russian, China and USA.
Based on public information on Solarwinds Hack and insight from Post Quantum Ltd
CEO Andersen Chang.
By Nick Ayton
Keywords: Analytics, Cybersecurity, Quantum Computing

 Testing Suez: Economics Are Driving Carriers Back Into the Red Sea
Testing Suez: Economics Are Driving Carriers Back Into the Red Sea Mastering Social Media in 2026: Optimizing Networking and Advocacy for the Digital Age
Mastering Social Media in 2026: Optimizing Networking and Advocacy for the Digital Age Friday’s Change Reflection Quote - Leadership of Change - Systemic Change Follows Failed Governance
Friday’s Change Reflection Quote - Leadership of Change - Systemic Change Follows Failed Governance Who Are You Under Pressure - And Is That the Real You?
Who Are You Under Pressure - And Is That the Real You? LinkedIn Voice for Sales
LinkedIn Voice for Sales