Jun23

The idea of submarine impulsion reminds me of how some security program functions. It's like a parallel between the two, where everything seems to be running smoothly, and suddenly, it all implodes.
Imagine being inside a submarine, relying on a complex propulsion system to navigate through water. Like the security program, it involves various mechanical and computational components to ensure everything is running as it should.
At first, the submarine and the company's security program operate seamlessly, fulfilling our respective roles effectively. The submarine moves forward, propelled by its powerful propulsion system, while a security program must diligently monitor and protect the system from potential threats, maintaining its integrity and stability.
However, life isn't without its challenges. In the case of the submarine, a malfunction or catastrophic failure within its propulsion system can lead to an implosion. Similarly, unforeseen vulnerabilities, an overwhelming surge of threats, or an internal flaw can trigger a similar implosion-like event for a company's security program.
When an implosion occurs within the security program, its protective mechanisms collapse or become overwhelmed. You lose the ability to detect and respond to threats effectively, potentially leading to breaches or a breakdown of the entire security infrastructure. It's like a sudden collapse, exposing the system to attacks, data breaches, or unauthorized access, which could result in significant damage or compromise of sensitive information.
Such implosions can be caused by various factors—ever-evolving cyber threats, zero-day vulnerabilities, inadequate security measures, or internal errors within an application's programming. Sometimes, it's a cascading failure, where a single vulnerability or flaw triggers a chain reaction that compromises the entire security system.
To prevent these implosions, you need constant evaluation and improvement. Staying updated with emerging threats, patching vulnerabilities regularly, conducting security audits, and implementing robust protocols are all crucial steps. Additionally, a layered defense strategy, with multiple security measures and redundant systems, helps mitigate the risk of catastrophic failure.
Understanding the causes and consequences of implosions is vital. It reminds me of the importance of being proactive, continuously improving my defenses, and staying vigilant to maintain the integrity and security of the systems you protect. Just like a submarine must ensure its propulsion system is functioning optimally, you must ensure that your security measures are always at their best to protect against potential implosions.
#cyber #data #security #programming #event #strategy #infrastructure #resilience #faulttolerance
Keywords: Business Continuity, Cybersecurity, Digital Transformation
 Lateral Moves: The Most Overlooked Succession Strategy in Companies
Lateral Moves: The Most Overlooked Succession Strategy in Companies The Asset Play: Timing, Structure & Global Arbitrage
The Asset Play: Timing, Structure & Global Arbitrage 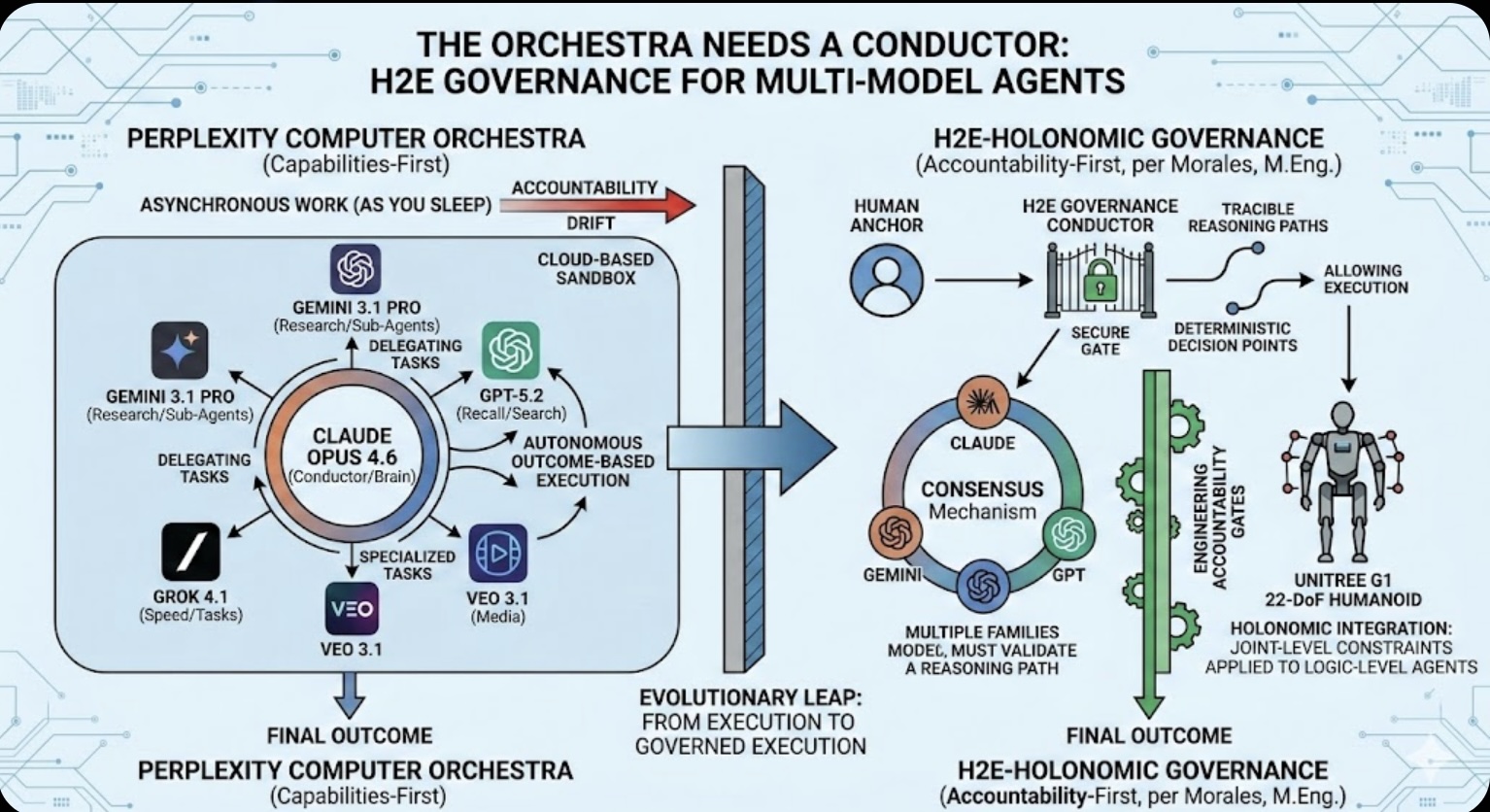 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business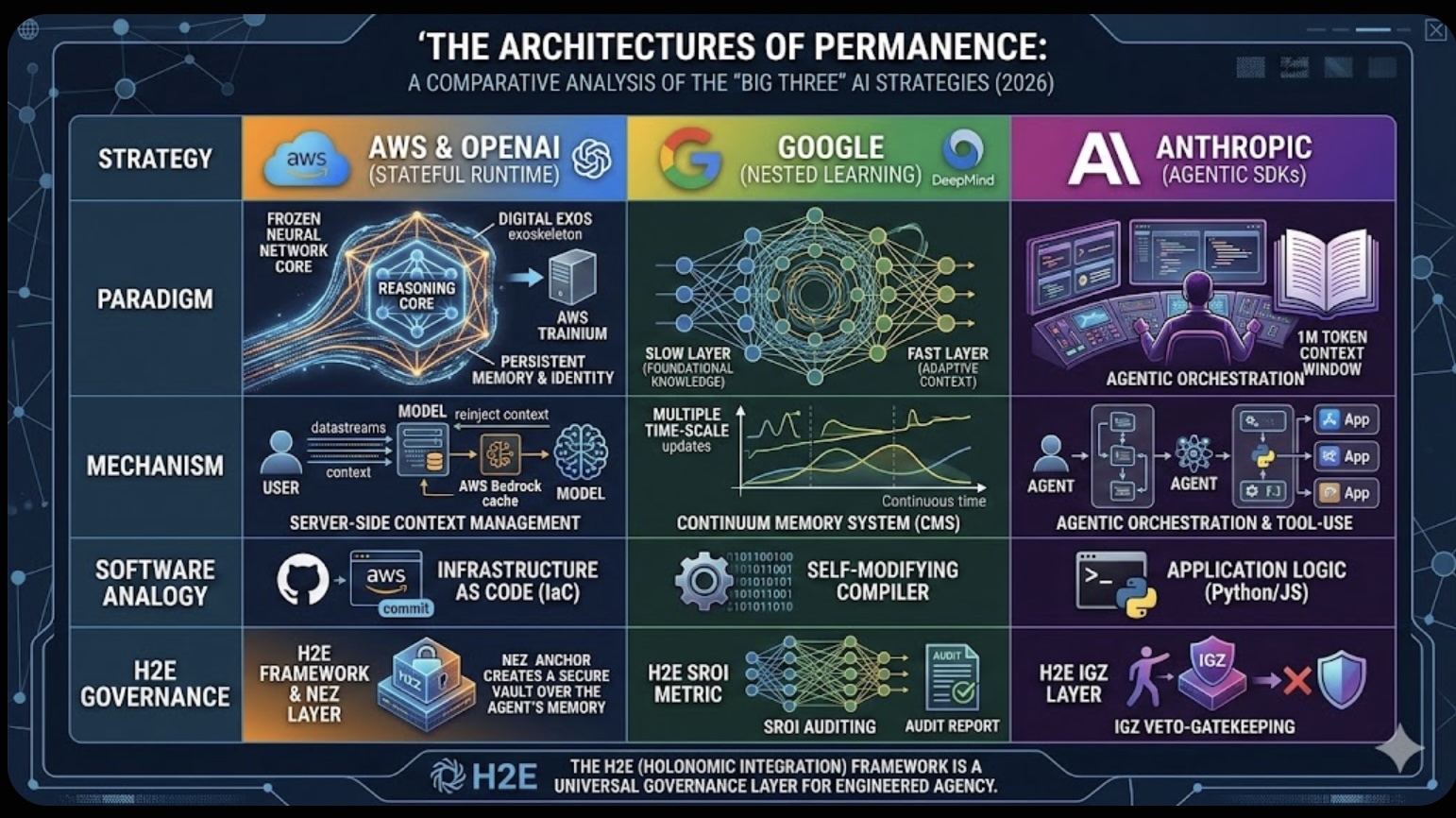 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)