Feb25

When I began focusing on network protection nearly twenty years ago, the job was largely about shielding servers and workstations. Now, technology has pushed us into an era where anything from industrial controllers to personal wearables can become a target. This shift expands the entryways available to malicious actors, making our daily work far more complex.
Studies project around 27 billion connected gadgets in operation by 2025. That projection signals an enormous rise in digital touchpoints that could be exploited if left unsecured. It is no longer enough to think about “traditional” networks when analyzing vulnerabilities; each small sensor or household appliance may become an unforeseen backdoor.
On one memorable trip to a modern production center, I witnessed a fully connected assembly line. Automated machines communicated seamlessly on the local network, and the ventilation and lighting systems were likewise controlled through online portals. Even the coffee dispensers were part of an integrated system. On the surface, it looked convenient, but each connected piece represented a new path that attackers could use to slip past defenses.
We have already seen real-world attacks illustrate this point. The Mirai botnet attack in 2016 gathered thousands of compromised IoT cameras and routers to cripple a major DNS provider, shaking online access across the United States. The most unsettling detail in that episode was the simplicity of the intrusion—default passwords left untouched.
In healthcare, the stakes grow higher. IoT pacemakers, insulin pumps, and imaging tools keep patients safe and healthy. Security flaws in these devices can lead to outcomes far more severe than data compromise.
Sometimes, the greatest danger lies in areas organizations fail to monitor. A fintech uncovered an internet-connected heating and cooling system that had not been reviewed by the IT team. The vendor responsible for maintenance had placed it online so they could easily run diagnostics from anywhere, but they did not impose any security restrictions. That single oversight could have given attackers a hidden route into critical financial systems.
IoT technology can also endanger privacy. Many new devices collect more than operational data; they might record speech, track individual users, or log personalized metrics. While assessing an office’s “smart” collaboration system, I discovered that it recorded parts of employees’ discussions for third-party analytics. This practice was not documented in contracts or manuals, leading to serious legal and ethical questions.
To handle the mounting risks that come with connected devices, the following framework has proved effective in my professional engagements:
Discover Everything
If you do not know a device exists, you cannot protect it. Regular scanning and asset inventories reveal what is active on your network. In nearly every security evaluation I have conducted, unidentified IoT units emerged—even in organizations known for strict policies.
Segment with Purpose
Think of segmentation like dividing a house into rooms with locking doors. Not everyone should enter sensitive zones. Network segmentation sets clear boundaries, mitigating the damage if one area is penetrated. In a healthcare project, subnetting isolated medical equipment from administrative workstations, minimizing the spread of threats.
Adopt Structured Updating
Servers often update automatically, but many IoT gadgets require manual patches. Plan these updates carefully to prevent downtime during critical operations. This includes establishing in-house guidelines for vendor firmware and creating assigned maintenance slots.
Apply Strict Authentication
Default or weak credentials are often enough to bring an entire system down. Insist on unique passwords for every device and consider token- or certificate-based methods for the units that handle sensitive data. This simple practice blocked several intrusion attempts in one large enterprise network I managed.
Watch for Irregularities
A defined baseline of normal network traffic provides a reference for spotting intrusions. AI-based detection can play a key part here, flagging abnormal data flow from devices that ordinarily have predictable communication patterns. When one retail chain applied an anomaly-monitoring solution, it caught a botnet attempting to add compromised devices to a criminal scheme.
AI has become a central issue in cybersecurity. Attackers now automate vulnerability scans or create deepfake content to trick employees. Over time, they will refine these techniques to disguise malicious activity so effectively that humans alone will struggle to detect intrusions.
On the defensive side, AI-based platforms capable of analyzing significant amounts of data in near real time. These solutions excel at absorbing complex patterns across numerous devices, finding issues in hours instead of weeks. Yet they require careful tuning and constant oversight, as a false positive could lead to unnecessary downtime.
This double-edged nature of AI prompts an essential question: how do we harness it for secure coordination without giving opponents free rein to create more dangerous attacks?
Connected devices are bringing enormous advantages, but they also create a wider zone for attack. Foresight, proactive scanning, disciplined management of credentials, and the judicious application of AI can shift the balance in your favor. Instead of blocking progress, security teams play a critical role in making sure advanced tools are used without inviting large-scale breaches.
Keywords: Cloud, IoT, IT Leadership
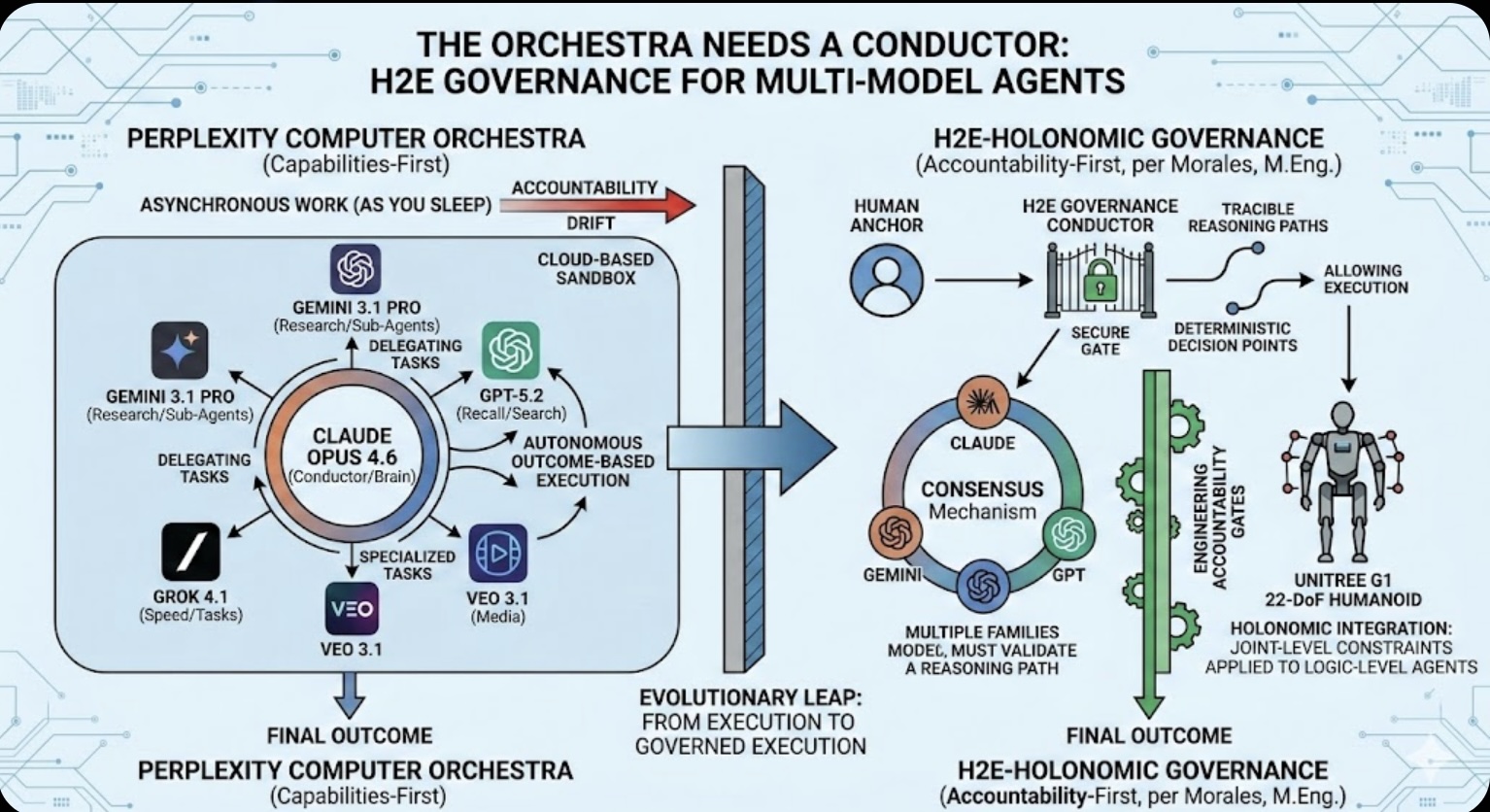 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business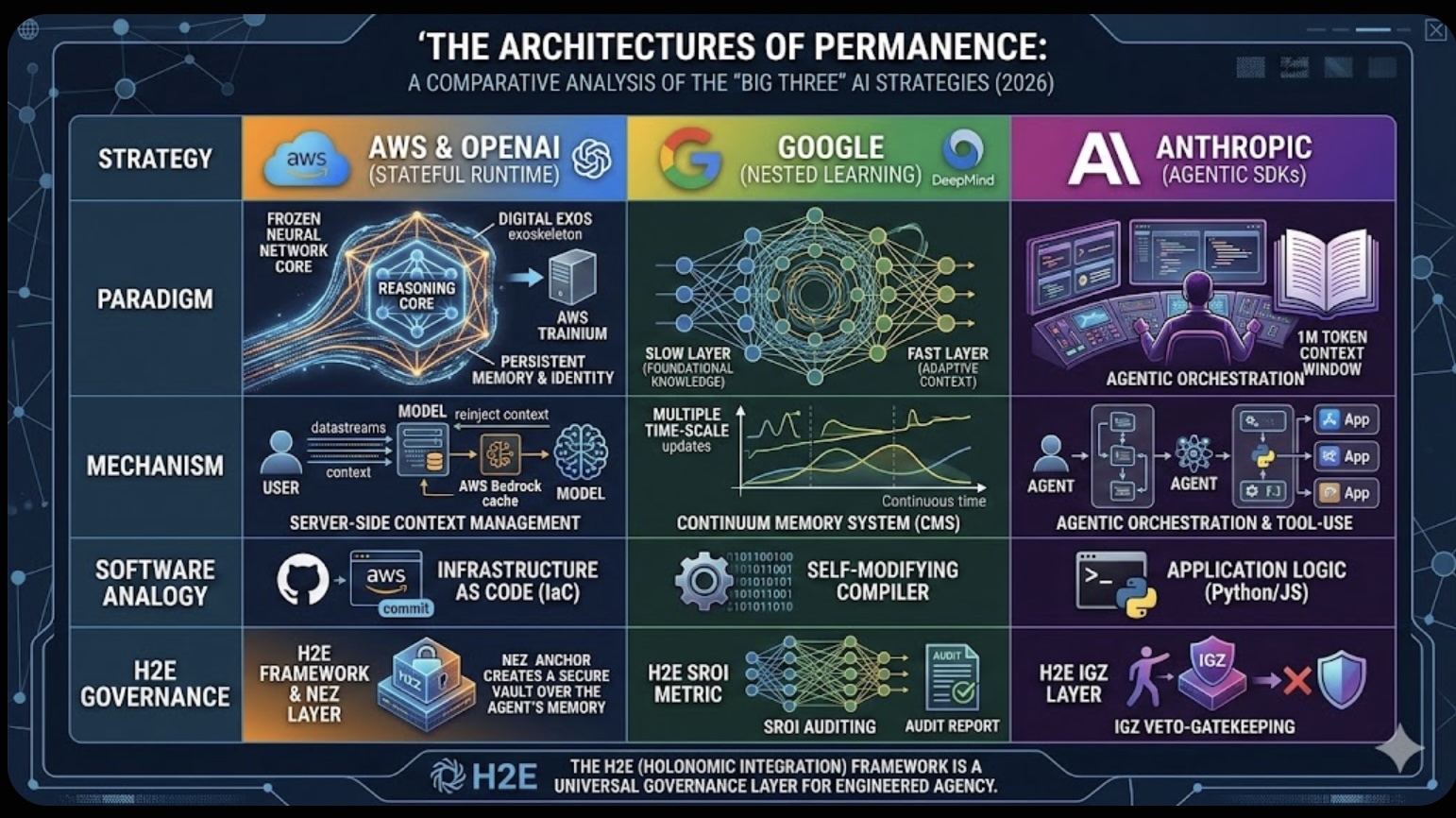 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026) Friday’s Change Reflection Quote - Leadership of Change - Change Leaders Enable Generational Advancement
Friday’s Change Reflection Quote - Leadership of Change - Change Leaders Enable Generational Advancement The Corix Partners Friday Reading List - February 27, 2026
The Corix Partners Friday Reading List - February 27, 2026