Information and Technology Risk Advisory Group
ISACA HQ
January 16, 2023
The I&T Risk Advisory Group will partner with ISACA Global to identify industry trends and support activities required to appropriately create the necessary information technology risk content to develop products in support of ISACA’s constituents. New product ideas will be discussed, and products will be prioritized in alignment with ISACA Global strategy.
See publication
Tags: Cybersecurity, Generative AI, Risk Management
Member of "2020 ISACA SheLeadsTech Ambassadors"
ISACA
March 14, 2020
SheLeadsTech's Ambassador program seeks to engage women in tech and those who support women in tech. The program is for our male allies, our advocates, our sponsors and mentors. It is for the human resources teams that make sure to have inclusive language in their job descriptions. It is for everyone who supports SheLeadsTech.
See publication
Tags: Cybersecurity, Privacy, Risk Management
Member of Advisory Group - Hong Kong Government Cyber Security Information Sharing Programme
OGCIO
December 06, 2018
Hong Kong's Office of the Government Chief Information Officer (OGCIO) was implementing the "Pilot Partnership Programme for Cyber Security Information Sharing" to enhance exchange of cyber security information with the industry and enterprises to jointly defend against cyber attacks.
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Time to revisit the risk level of insider threat
Time to revisit the risk level of insider threat
LinkedIn
August 31, 2020
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Volkswagen Group becomes the new victim of ransomware
Volkswagen Group becomes the new victim of ransomware
LinkedIn
August 29, 2020
A Volkswagen Dealership Has Been Hit by “Conti” Ransomware
See publication
Tags: Cybersecurity, Privacy, Risk Management
 New Experience to attend 12th InfoSecurity Virtual Summit
New Experience to attend 12th InfoSecurity Virtual Summit
LinkedIn
August 28, 2020
It has been a new and impressive experience to virtually-attend the 12th InfoSecurity Virtual Summit 2020 with a virtual lobby, an exhibition hall, a conference and a networking lounge. The quiz and showcase game are wonderful ideas to engage the attendees.
The two sessions of the panel discussion are informative and insightful.
Looking forward to participate the Part II of the Summit on 11th Sept 2020. https://lnkd.in/gXmpiPv
Don't let WFH stop your professional development journey.
See publication
Tags: Cybersecurity, Future of Work, Privacy
 MITRE Attack frameworks for Industrial Control Systems TTPs
MITRE Attack frameworks for Industrial Control Systems TTPs
Cybersec Hub HK
August 25, 2020
The MITRE ATT&CK framework is a comprehensive matrix of tactics and techniques used by threat hunters, red teamers, and defenders to better classify attacks and assess an organization's risk. Many of you may already reference it, as it is aimed is to improve post-compromise detection of adversaries in enterprises by illustrating the actions an attacker may have taken.
MITRE now released an ATT&CK knowledge base for the industrial control systems (ICS). It includes the tactics and techniques that cyber adversaries use when attacking the industrial control systems (ICS), while the knowledge base can be used to better characterize and describe post-compromise adversary behavior.
Please refer to this link for full details https://collaborate.mitre.org/attackics/index.php/Main_Page
See publication
Tags: Cybersecurity
 Privacy guidance for manufacturers of Internet of Things devices
Privacy guidance for manufacturers of Internet of Things devices
LinkedIn & Twitter
August 22, 2020
If your IoT device will handle Canadian personal information, please read this privacy guidance issued by Officer of Privacy Commissioner of Canada to understand what regulatory requirements from PIPEDA will impose on your products.
See publication
Tags: Cybersecurity, IoT, Privacy
 Sodinokibi (REvil) ransomware is now targeting to energy sector
Sodinokibi (REvil) ransomware is now targeting to energy sector
LinkedIn & Twitter
July 03, 2020
After preying on healthcare, services and food sectors, the threat actor behind the Sodinokibi (REvil) ransomware is now targeting to energy sector.
Symantec report in late June -> https://lnkd.in/grDtndY
The ransomware operators demanded $14 million from power company - https://lnkd.in/giQridD https://lnkd.in/gAwgMFV
See publication
Tags: Cybersecurity, Risk Management, Business Continuity
 Looking forward to the launch of IoT device Security Trust Mark Certification
Looking forward to the launch of IoT device Security Trust Mark Certification
LinkedIn
June 22, 2020
Looking forward to the launch of this IoT device Security Trust Mark Certification, which gives consumer confidence and purchase indicator on IoT home appliances.
The testing program will have two phases. First, manufacturers will develop a statement of claims, describing security, safety and privacy aspects of a device. Those could include "baseline" aspects, such as policies on default passwords, how encryption is used and how the device can be patched. They also could include information about specific security features, such as how the device securely transmits personal data..
In the second phase, an accredited test facility will verify the manufacturer's claims and issue a letter of recommendation.
See publication
Tags: Cybersecurity, IoT, Privacy
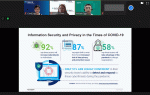 Business Continuity Plan for the New Normal
Business Continuity Plan for the New Normal
ISACA China and Hong Kong Chapter
June 16, 2020
I am thrilled to be MC of ISACA China Hong Kong Chapter's Webinar "Business Continuity Plan for the New Normal". Inspired by William Tam on the crucial security considerations in "new normal" BCP under cloud acceleration and workplace redefine.
The latest security product trend - SASE "Secure Access Service Edge" has been covered. See more about SASE definition from Gartner. https://lnkd.in/gRDmJcX
See publication
Tags: Cybersecurity, Change Management, COVID19
California Consumer Privacy Act has taken effect
twitter & LinkedIn
June 06, 2020
California Consumer Privacy Act has officially taken effect. Check out what you should note.
Even if your organization does not have physically entity in the state of California, does not mean this act is applicable to you. The CCPA applies to any for-profit entities that both collect and process the personal information of California residents.
organization meets any one of the following criteria has to comply with the regulation:
- business generates annual gross revenue in excess of $25 million
- business receives or shares personal information of more than 50,000 California residents annually
- business derives at least 50 percent of its annual revenue by selling the personal information of California residents
See publication
Tags: Cybersecurity, Privacy, Risk Management
Lesson Learnt from Mercedes-Benz data leak
Twitter & LinkedIn
May 26, 2020
Lesson learnt from Mercedes-Benz data leak —— set controls on your shared program code repositories GITHUB
See publication
Tags: Cloud, Cybersecurity, IoT
Review: Comparing 5 popluar video-conferencing solutions - Zoom, Cisco Webex, Microsoft Teams, GoToMeeting, and Google Meet
Cybersec Hub HK
May 04, 2020
“Cybersechub.hk” is a community-driven cyber security information sharing and collaborative platform that enables online relationships and connections among participating organisations (Members) for sharing cyber security information, such as cyber threats and vulnerabilities. “Cybersechub.hk” is operated based on the principles of trust, openness, transparency and collaboration among Members.
See publication
Tags: Business Continuity, Cybersecurity, Privacy
Cybersecurity and Resiliency Observations - Published by US SEC
Cybersec Hub HK
February 05, 2020
“Cybersechub.hk” is a community-driven cyber security information sharing and collaborative platform that enables online relationships and connections among participating organisations (Members) for sharing cyber security information, such as cyber threats and vulnerabilities. “Cybersechub.hk” is operated based on the principles of trust, openness, transparency and collaboration among Members.
See publication
Tags: Cybersecurity, Privacy, Risk Management
Samsung S10 Security Advisory - Disable fingerprint authentication/payment Options on your Bank Apps
Cybersec Hub HK
October 28, 2019
“Cybersechub.hk” is a community-driven cyber security information sharing and collaborative platform that enables online relationships and connections among participating organisations (Members) for sharing cyber security information, such as cyber threats and vulnerabilities. “Cybersechub.hk” is operated based on the principles of trust, openness, transparency and collaboration among Members.
See publication
Tags: Cybersecurity, Privacy, Risk Management
Singapore CSA’s OT Cybersecurity Masterplan
Cybersec Hub HK
October 02, 2019
“Cybersechub.hk” is a community-driven cyber security information sharing and collaborative platform that enables online relationships and connections among participating organisations (Members) for sharing cyber security information, such as cyber threats and vulnerabilities. “Cybersechub.hk” is operated based on the principles of trust, openness, transparency and collaboration among Members.
See publication
Tags: Cybersecurity, Privacy, Risk Management
Ponemon Institute report finds that cyberattacks on the OT are increasing
LinkedIn
September 30, 2019
A new report, compiled by the manufacturing company Siemens and the Ponemon Institute finds that cyberattacks on the OT are increasing.
See publication
Tags: Cybersecurity, IoT, Risk Management
State of Cybersecurity 2019 report released
LinkedIn
July 01, 2019
The short supply of qualified cybersecurity professionals has led to unfilled positions and a widening work skills gap in our industry.
ISACA released study reports for past few years. The latest 2019 State Of Cybersecurity Report Part 1 & 2 have been released now!
Part 1 of ISACA’s State of Cybersecurity 2019 report analyzes the trends of cybersecurity hiring, retention, gender diversity and budget implications.
The report highlighs:
- Cybersecurity professionals are still in short supply and hard to find, particularly for roles that require technical proficiency.
- Retaining cybersecurity professionals is exceptionally difficult, even when enticements such as training and certification are provided.
- Gender diversity programs are declining and perceived as less effective than in the past.
- Cybersecurity budget increases are expected to slow slightly.
Part 2 of the reports examines threat landscape, including attack volumes and vectors.
See publication
Tags: Cybersecurity, Diversity and Inclusion, Risk Management
British Airways Data Breach Case Study Analysis
Cybersec Hub HK
September 28, 2018
“Cybersechub.hk” is a community-driven cyber security information sharing and collaborative platform that enables online relationships and connections among participating organisations (Members) for sharing cyber security information, such as cyber threats and vulnerabilities. “Cybersechub.hk” is operated based on the principles of trust, openness, transparency and collaboration among Members.
See publication
Tags: Cybersecurity, Privacy, Risk Management
7 Keys to Strengthen Your Security Culture
Twitter
September 05, 2017
Great article on 7 Keys to Strengthen Your Security Culture.. adopt change mgt methodology in cybersafe programme.
See publication
Tags: Change Management, Culture, Cybersecurity
The EU-US Privacy Shield agreement declared INVALID
LinkedIn & Twitter
December 31, 1969
The EU-US Privacy Shield agreement that attempts to guarantee the secure transmission of EU data to the United States, has been declared INVALID by the Court of Justice of the European Union (CJEU).
The ruling based on a Privacy advocate (Max Schrems) challenged the agreement, arguing that US national security laws did not protect EU citizens from government surveillance.
All EU companies has data transfer to US should reassess the situation. Affected companies will now have to sign "standard contractual clauses": non-negotiable legal contracts drawn up by Europe, which are used in other countries besides the US.
See publication
Tags: Cybersecurity, Privacy, National Security
"Security Leader of the Year" 2023 - Women in IT Asia Award
DiversityQ
June 19, 2023
The "Security Leader of the Year" award recognised and celebrated a woman CSO, CISO or any other senior IT security function (including cyber security and data management), who has delivered outstanding work, implemented innovative approaches to security and contributed to the impact of policies, procedures and projects within the business.
See publication
Tags: Cybersecurity, Security
Global 100 CEH (Certified Ethical Hacker) Hall of Fame 2021
EC-COUNCIL
May 17, 2021
EC-Council, the world’s leading ethical hacking certification body, has announced the Certified Ethical Hacker (CEH) Hall of Fame of 2021, listed the top 100 awardees across the globe. The Hall of Fame celebrates some of the most accomplished Certified Ethical Hackers, helping organizations with cybersecurity teams access the best talent worldwide and benchmark their teams’ capability against the best in the industry.
The top 100 members of the CEH Hall of Fame of 2021 have been selected based on their professional achievements and community contributions.
See publication
Tags: Cybersecurity
Active Contributors to Cybersechub.hk
cybersechub.hk
October 01, 2019
Named Active Contributors in Nov 2019
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Hong Kong Cyber Security Professionals Awards 2016
Hong Kong Cyber Security Professionals Awards 2016
Hong Kong Police Force
January 06, 2016
My honour to receive the Gold Management Award under Utility Category.
See publication
Tags: Cybersecurity, Diversity and Inclusion, Privacy
 Remote Workforce Security: Protecting People, Protecting the Enterprise
Remote Workforce Security: Protecting People, Protecting the Enterprise
The 12th Annual InfoSecurity Virtual Summit 2020
September 11, 2020
Carrying the theme of “Redefining Cyber Security in The Age of Insecurity”, the 12th Annual InfoSecurity Summit 2020, as the industry’s most important annual meeting for Information Security leaders and professionals, will bring together a galaxy of influential and disruptive Cyber Security Experts and thought leaders to share the latest information security trends and emerging technologies to thwart cyber attacks. Specially designed for Information Security Decision Makers & Professionals Across All Industries, this summit will unveil effective approaches to defense and lay out a roadmap for enterprise to prepare for tomorrow’s New Forms of Attack.
See publication
Tags: Cybersecurity, Privacy, Security
 Emerging Security Threats
Emerging Security Threats
Information Security Summit 2019
October 24, 2019
The Information Security Summit - Over the Horizon Cyber Security is a Regional Event with the aim to give participants from the Asia Pacific region an update on the latest development, trends and status in information security.
As cyber attackers are growing more capable and smarter, enterprises are looking at investing in analytics and threat intelligence in order to make better decisions on investment in cyber defense to
pre-empt the attacks. Advanced security technologies are increasingly integrated with threat intelligence. Overseas and Local Experts from the industry were invited to share their experience and knowledge in the panel discussion.
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Rethinking the Future of Cyber Battles - How to Supercharge Your Cyber Defense?
Rethinking the Future of Cyber Battles - How to Supercharge Your Cyber Defense?
ConnecTechAsia Summit 2019
June 18, 2019
In the past, Cyber-attack confined with enterprises and homes. Incidents are mostly occurring in IT systems. Today, the nature of threats has evolved. "Advanced threats" are not just hard to detect, are they also targeting at IoT/Smart Devices and Industrial Control System (ICS). How ready are the community and industry in countering such new level and new sophistication of cyber threats? This panel discussion gathered a plenary of moderator and practitions with whole wealth of experiences to share their thoughts on the topic.
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Preparing for The Future Enterprise - Evaluating the New Security, Data Protection & Cyber Challenges
Preparing for The Future Enterprise - Evaluating the New Security, Data Protection & Cyber Challenges
CISO Roundtables
November 27, 2018
The 2nd CISO Executive Roundtables Hong Kong carried the theme of "Preparing for The Future Enterprise - Evaluating the New Security, Data Protection & Cyber Challenges". It served as an important platform for CISOs and IT security leaders to gain access to the latest threat landscapes, cyber risk intelligence and cybersecurity capabilities, and discover new and innovative solutions.
See publication
Tags: Cybersecurity, Digital Transformation, Risk Management
 Rethinking the Role of Technology (Cybersecurity, Insider Threat and Regulatory Requirements)
Rethinking the Role of Technology (Cybersecurity, Insider Threat and Regulatory Requirements)
ISACA China and Hong Kong Chapter
March 22, 2018
The theme of ISACA Annual Conference 2018 was "Managing Risk and Security for the Technology Transformation". Disruptive technologies challenge the basic principles of information risk and security management. Corporate management and technology leaders or even a citizen must understand the risks associated with the technological innovations, and balance the imperative to protect them with the need to adopt ever-changing and innovative technology approaches.
In the panel discussion I joined, I shared some real-life threats and risks (e.g. phishing, API, security architecture impacted by privacy/cybersecurity laws) to organizations with latest technologies.
See publication
Tags: Cybersecurity, Privacy, Risk Management
 Perspectives and Challenges on achieving Business Values in Cyber Security
Perspectives and Challenges on achieving Business Values in Cyber Security
Information Security Summit 2016
September 13, 2016
I joined as one of panels in this panel discussion at the Information Security Summit 2016. I shared my view on how cyber security should align with business strategy, and facilitate business to secure key assets. I also recommended to incorporate change management methodology into security programme.
See publication
Tags: Change Management, Cybersecurity, Privacy
 Seasonings to Improve Sustainability of your Information Security Programme in new Digital Age
Seasonings to Improve Sustainability of your Information Security Programme in new Digital Age
OGCIO
September 27, 2020
Choosing international/ industry best practice information security frameworks (e.g.ISO/IEC27000 family, COBIT, CIS, NIST CSF) helps information security practitioners to identify the key ingredients (scope, objectives, security and control requirements, etc.) of any IT/OT Security Programme. However, the new normal has forced many organizations to go online or go for cloud in an exponential rate. To put your programme into actionable and sustainable for years, it will take some seasonings to improve the flavor. In this sharing, Carol would provide her key seasoning tips to balance risks, protection, talent shortage and cost in a popular information security programme amongst stakeholders.
See publication
Tags: Change Management, Cybersecurity, Digital Transformation
 Promoting Partnership and Collaboration for Cyber Security Information Sharing
Promoting Partnership and Collaboration for Cyber Security Information Sharing
OGCIO
December 06, 2018
Hong Kong's Office of the Government Chief Information Officer (OGCIO) was implementing the "Pilot Partnership Programme for Cyber Security Information Sharing" to enhance exchange of cyber security information with the industry and enterprises to jointly defend against cyber attacks.
My topic shared my experience and benefits of collaboration in order to build security awareness in public community and knowledge sharing practices within industry peers.
See publication
Tags: Change Management, Cybersecurity, Risk Management
 The 2nd Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
The 2nd Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
CNNPN
May 24, 2018
This Symposium was organized by 4 power utilities in Southern China region, which aimed to promote the cyber security best practice sharing amongst peers.
See publication
Tags: Cybersecurity, Future of Work, Risk Management
 Battling Against Cybercrime: Recipe for Driving a cyber-safe culture
Battling Against Cybercrime: Recipe for Driving a cyber-safe culture
HTCIA
December 06, 2017
I delivered this talk in 11th Annual HTCIA Asia Pacific Training Conference. A latest trend on cybercrime was shared. And also explained how change management methodology should be applied in security programme.
See publication
Tags: Change Management, Cybersecurity, Risk Management
 Recipe for a Successful Cyber Safe Awareness Campaign
Recipe for a Successful Cyber Safe Awareness Campaign
ISC2
September 21, 2017
I shared this Case Sharing talk in the “SecureSingapore 2017” conference organized by ISC2 to security professionals in Singapore. I showcased how a real-life security programmed adopted ADKAR change management methodology to cultivating an organization-wide cyber risk awareness.
See publication
Tags: Cybersecurity, Change Management, Risk Management
 The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
CLP
June 26, 2017
This Symposium was organized by 4 power utilities in Southern China region, which aimed to promote the cyber security best practice sharing amongst peers.
See publication
Tags: Cybersecurity, Change Management, Risk Management
 Recipe for a Successful Cyber Safe Awareness Campaign
Recipe for a Successful Cyber Safe Awareness Campaign
Hong Kong Productivity Council and OGCIO
November 25, 2016
I shared this Case Sharing talk in the “Build a Secure Cyberspace 2016” seminar organized by Hong Kong Productivity Council and OGCIO. I explained how change management methodology can be applied in security programme by cultivating cyber risk awareness.
See publication
Tags: Change Management, Cybersecurity, Risk Management
 Security Challenges for Critical Infrasstructure
Security Challenges for Critical Infrasstructure
ISC2 - Secure HongKong 2015
September 11, 2015
This talk was delivered in my capacity of Cyber Risk Manager at CLP Power HK Ltd. to share difference in key priority of 3 information security attributes (Confidentiality, Integrity, Availability) in general IT systems, industrial control systems and Smartgrid.
See publication
Tags: Cybersecurity, Privacy, Risk Management


 Time to revisit the risk level of insider threat
Time to revisit the risk level of insider threat
 Volkswagen Group becomes the new victim of ransomware
Volkswagen Group becomes the new victim of ransomware
 New Experience to attend 12th InfoSecurity Virtual Summit
New Experience to attend 12th InfoSecurity Virtual Summit
 MITRE Attack frameworks for Industrial Control Systems TTPs
MITRE Attack frameworks for Industrial Control Systems TTPs
 Privacy guidance for manufacturers of Internet of Things devices
Privacy guidance for manufacturers of Internet of Things devices
 Sodinokibi (REvil) ransomware is now targeting to energy sector
Sodinokibi (REvil) ransomware is now targeting to energy sector
 Looking forward to the launch of IoT device Security Trust Mark Certification
Looking forward to the launch of IoT device Security Trust Mark Certification
 Business Continuity Plan for the New Normal
Business Continuity Plan for the New Normal
 Member of Subject Matter Expert Reviewers - ISACA 2020 CDPSE Review Manual
Member of Subject Matter Expert Reviewers - ISACA 2020 CDPSE Review Manual
 Hong Kong Cyber Security Professionals Awards 2016
Hong Kong Cyber Security Professionals Awards 2016
 Remote Workforce Security: Protecting People, Protecting the Enterprise
Remote Workforce Security: Protecting People, Protecting the Enterprise
 Emerging Security Threats
Emerging Security Threats
 Rethinking the Future of Cyber Battles - How to Supercharge Your Cyber Defense?
Rethinking the Future of Cyber Battles - How to Supercharge Your Cyber Defense?
 Preparing for The Future Enterprise - Evaluating the New Security, Data Protection & Cyber Challenges
Preparing for The Future Enterprise - Evaluating the New Security, Data Protection & Cyber Challenges
 Rethinking the Role of Technology (Cybersecurity, Insider Threat and Regulatory Requirements)
Rethinking the Role of Technology (Cybersecurity, Insider Threat and Regulatory Requirements)
 Perspectives and Challenges on achieving Business Values in Cyber Security
Perspectives and Challenges on achieving Business Values in Cyber Security
 Seasonings to Improve Sustainability of your Information Security Programme in new Digital Age
Seasonings to Improve Sustainability of your Information Security Programme in new Digital Age
 Promoting Partnership and Collaboration for Cyber Security Information Sharing
Promoting Partnership and Collaboration for Cyber Security Information Sharing
 The 2nd Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
The 2nd Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
 Battling Against Cybercrime: Recipe for Driving a cyber-safe culture
Battling Against Cybercrime: Recipe for Driving a cyber-safe culture
 Recipe for a Successful Cyber Safe Awareness Campaign
Recipe for a Successful Cyber Safe Awareness Campaign
 The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
 Recipe for a Successful Cyber Safe Awareness Campaign
Recipe for a Successful Cyber Safe Awareness Campaign
 Security Challenges for Critical Infrasstructure
Security Challenges for Critical Infrasstructure
 Webinar - Revamp your Incident Response Plan for the new Normal
Webinar - Revamp your Incident Response Plan for the new Normal
 Professional Development Seminar -- Why Hardened Security is Vital by Mr. Ian Christofis
Professional Development Seminar -- Why Hardened Security is Vital by Mr. Ian Christofis
 Professional Development Seminar -- Story-telling – the Art of Creating Business Case and Attention on Things that Really Matters
Professional Development Seminar -- Story-telling – the Art of Creating Business Case and Attention on Things that Really Matters
 ISACA Asia Pacific CACS Conference 2019
ISACA Asia Pacific CACS Conference 2019
 The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium
The 1st Guangdong, Hong Kong, Macau Power Industry Cyber Security Symposium