

Naveen Kumar Yeliyyur Rudraradhya serves as Supervisor of IT Network Security at WLK in Houston. With over 21+ years of international experience, he is a senior information security specialist with deep expertise in Identity and Access Management (IAM) and cybersecurity. He specializes in designing, creating, and implementing global cybersecurity and identity & access management frameworks across consumer and industrial sectors. Known for translating complex IAM challenges into actionable security strategies, he guides organizations in securing digital assets, deploying robust identity governance solutions, and designing enterprise-grade security systems that address evolving threats while maintaining operational efficiency.
| Naveen Kumar Yelliyyur Rudraradhya | Points |
|---|---|
| Academic | 0 |
| Author | 14 |
| Influencer | 1 |
| Speaker | 0 |
| Entrepreneur | 0 |
| Total | 15 |
Points based upon Thinkers360 patent-pending algorithm.
 Building Global Identity Access Management That Works: Lessons from Automation, Standardization, and Compliance
Building Global Identity Access Management That Works: Lessons from Automation, Standardization, and Compliance
Tags: IT Leadership, IT Operations, IT Strategy
Tags: Cybersecurity, Education, Security
Tags: AI, AI Governance, Cybersecurity
 AI and Machine Learning in IAM: Shaping the Future of Enterprise Security
AI and Machine Learning in IAM: Shaping the Future of Enterprise Security
Tags: Cybersecurity, Design Thinking, Leadership
 IAM Cloud Security Guidebook
IAM Cloud Security Guidebook
Tags: Cybersecurity, IT Leadership, IT Operations
Tags: Cybersecurity, IT Strategy, Leadership
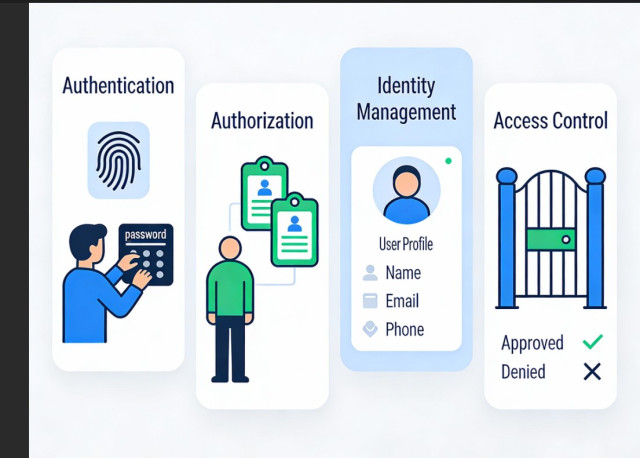 A Beginner's Guide to Identity and Access Management Key Concepts
A Beginner's Guide to Identity and Access Management Key Concepts
Tags: Cybersecurity, Design Thinking, IT Leadership
 Building Global Identity Access Management That Works: Lessons from Automation, Standardization, and Compliance
Building Global Identity Access Management That Works: Lessons from Automation, Standardization, and Compliance IAM Cloud Security Guidebook
IAM Cloud Security Guidebook Keep Your Identity Safe This Holiday Season!!
Keep Your Identity Safe This Holiday Season!!