NimbusNet: Building a High‑Performance Echo & Chat Server Across Boost.Asio and Io_uring
HackerNoon
May 21, 2025
We design and benchmark a cross‑platform echo & chat server that scales from laptops to low‑latency Linux boxes. Starting with a Boost.Asio baseline, we add UDP and finally an io_uring implementation that closes the gap with DPDK‑style kernel‑bypass—all while preserving a single, readable codebase.
See publication
Tags: Architecture, Engineering
Why do we sometimes need `explicit`?
Import from medium.com
April 23, 2025
Thumb-rule: In C++ any constructor that has only one argument is considered as a ‘conversion’ constructor. This implies that the compiler is allowed to turn the argument into an object of your class without ‘you’ asking for it.https://medium.com/media/32b22bead3a2c384132a4cbe72851779/hrefHe
See publication
Tags: Architecture
Frequent recipes for 2D Matrices
Import from medium.com
August 28, 2023
Frequent Recipes for 2D MatricesParsing 2D matrices is one of the fundamental skills in problem solving.Let’s go through some of the frequently used methods used when interacting with 2D matrices. For the case of conciseness and simplicity, the following snippets are going to be in python.For o
See publication
Tags: Architecture
Why do we need to index data? | Database Storage & Retrieval
Import from medium.com
August 10, 2023
Note: This article highlights the needs for indexing when dealing with databases. These are notes (and) broad takeaways from Chapter-3 of Design of Data Intensive Applications book. Added some python code for understanding.Link to the book: Design of Data Intensive ApplicationsWhy is this relevant?W
See publication
Tags: Architecture
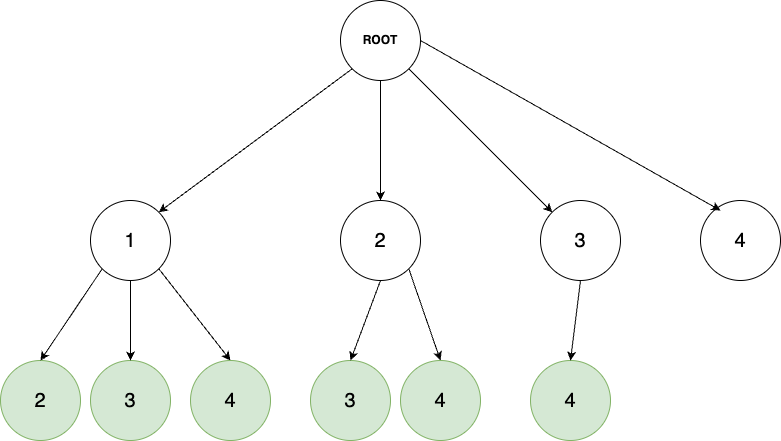 Template for Backtracking Problems — (Part1: The Basics)
Template for Backtracking Problems — (Part1: The Basics)
Import from medium.com
August 09, 2023
Template for Backtracking Problems — (Part1: The Basics)Backtracking problems have always been interesting to me, and in this article, we are going to go through a few problems that can get us started on journey of mastering backtracking problems.In the problems categorized as backtracking,:W
See publication
Tags: Architecture
CSES Series | Introductory Problems Set | Gray Code
Import from medium.com
July 06, 2023
Problem Statement: https://cses.fi/problemset/task/2205/Explanation of Solution:What is gray code as defined by the problem?Gray code is a list of 2^n bit strings of length n, where any 2 successive strings exactly differ by one bit. To be more specific, their hamming distance is 1Hence when we co
See publication
Tags: Architecture
How to recursively crawl folders using python?
Import from medium.com
March 28, 2021
Background: I have been asked this question in interviews, quite a few times, hence I felt, this deserved a write-up. So let’s get started.Problem Statement: Print the folders and files in a directory recursively.Solution:There are few ways to approach this:a. Use the os module in python to walk
See publication
Tags: Architecture
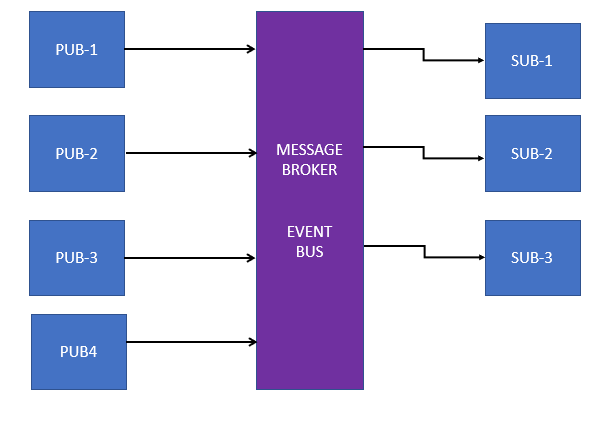 Publisher-Subscriber model fundae
Publisher-Subscriber model fundae
Import from medium.com
September 21, 2020
Publisher-Subscriber model model also known as Pub-Sub model is one of the widely used design patterns and is commonly used in messaging systems, embedded middleware and notification systems. In this article we are going to comprehend the pub-sub model, understand the basics, it’s multiple impleme
See publication
Tags: Architecture
When Emotions become Tangible?
Import from medium.com
August 02, 2018
Photo by Jeremy Thomas on UnsplashAmma ~ The Queen’s LandingThe word ‘Amma’ (Mom) and all it’s variants screams of emotions. If I have to name some of the strongest individuals in my life, my mother would top the list. Right now, if I consider myself to be mentally strong , a good chunk o
See publication
Tags: Architecture
The Moment One Finally Changes! — Impressions.
Import from medium.com
July 07, 2018
“The silhouette of a man standing on a rock during sunset at Shenandoah National Park” by Bryan Minear on UnsplashWhat keeps me moving?The rain outside looks beautiful. I try to get up, yet decide to sleep for another hour until the sun shows up. The sunlight spilling from the half-open blinds
See publication
Tags: Architecture
Cloud Security and Data Protection in Hybrid Environments: Strategies, Challenges, and Best Practices
IGI Global Publishing
April 14, 2025
The hybrid cloud environments, which include on-premises, private, and public clouds, come with numerous security implications, including data sovereignty, compliance regulations, and the problem of multi-cloud. The security issues above indicate that existing traditional security frameworks are inadequate. This chapter provides a detailed analysis of how to protect hybrid cloud models and data in general. This entails implementing a zero-trust security model, strong identity access management (IAM) measures, and network segmentation as enablers to the risks. Advanced data security approaches include encryption, tokenization, and compliance with regional and international laws and regulations, including GDPR and HIPAA. Expanding the discussion to novel technologies like AI, machine learning, and blockchain applications and their function in improving threat identification, response automation, and data integrity. Real use cases showcase guidelines for using hybrid cloud security effectively and analyze lessons that can be learned from cyber-attacks.
See publication
Tags: Architecture, Cybersecurity, DevOps
Personalized Healthcare Monitoring Through AR Wearables and Predictive Analytics Algorithms
2025 First International Conference on Advances in Computer Science, Electrical, Electronics, and Communication Technologies (CE2CT)
April 02, 2025
Wearable Augmented Reality integrated with predictive analytics is revolutionizing the healthcare monitoring system innovative and individualized. This paper outlines a new paradigm integrating AR devices for capturing and, especially, showing user health statistics and using algorithms to predict health issues. The AR visualization integration with data analytics ensures that users can observe important signs such as pulse, blood oxygen, and activity in real-time. Some of them are device calibration, synchronized data, and the prophecy of the model that forms the framework's design to provide a sound professional health monitoring system. The users' data is submitted to the comprehensive predictive analytics algorithms to define certain patterns to create specific recommendations and ensure early health management. The performance analysis shows a high percentage of system accuracy, and the provided findings show its effectiveness during clinical application or everyday use. This approach reflects a major advancement in improving healthcare delivery by employing innovative wearable technology and data analysis.
See publication
Tags: AR/VR, Predictive Analytics, Security
Securing Cloud AI Workloads: Protecting Generative AI Models from Adversarial Attacks
IEEE, 2025 IEEE 4th International Conference on AI in Cybersecurity (ICAIC)
January 29, 2025
Generative artificial intelligence models have brought about advancements in fields like healthcare and finance, as well as in autonomous systems; however, they also encounter notable security vulnerabilities, primarily when operating in cloud environments. These AI models can be targeted by attacks that involve altering input data to deceive the system into generating harmful or incorrect results. This study delves into the security issues that AI systems face in cloud setups, explicitly focusing on the dangers posed by adversarial manipulation of data integrity and the challenges of utilizing shared resources within multi-user environments. The text covers methods for defending AI models, like training and defensive distillation, to make them more robust against attacks.
See publication
Tags: Cloud, Cybersecurity, DevOps
Generative AI for Automated Security Operations in Cloud Computing
2025 IEEE 4th International Conference on AI in Cybersecurity (ICAIC)
January 29, 2025
New opportunities in cloud computing have brought many new risks that require effective protection of dynamic distributed environments. Introducing a new formative technology, generative AI, to cloud security has far-reaching benefits for automating threat detection, real-time incident addressing, and vulnerability management. This paper focuses on extending generative AI with cloud security tools like AWS GuardDuty and Google Cloud Security Command Center; the contemplation of accuracy enhancement and response efficiency highlights its aim. Concerning actual applications such as SOAR systems, the study demonstrates how media industry giants, such as Netflix and JPMorgan Chase, have used AI to minimize risk factors while increasing operational efficiency.
See publication
Tags: Cybersecurity, DevOps, Generative AI
Optimizing Service Deployments With NLP Based Infrastructure Code Generation-An Automation Framework
2024 IEEE 2nd International Conference on Electrical Engineering, Computer and Information Technology (ICEECIT)
December 22, 2024
In this paper we discuss how we combine natural language processing (NLP) techniques and infrastructure as code (IaC) tools like Terraform; to build a framework that converts natural language queries into Terraform code, enabling users to generate multi-cloud infrastructure configurations. We detail the construction of the NLP engine, the implementation for benchmarking various context-aware models, and the validation and execution of code, which leads to the integration of the model with DevSecOps pipelines. For benchmarking, we test models such as RoBERTa, GPT-4, T5 and Llama on their performance in terms of accuracy, latency and capacity to translate complex infrastructure requirements given as conversational queries into deployable terraform configuration. On one hand, this framework enhances the accessibility and efficiency of writing Terraform code (TF-code), while on the other, it results in a 73% reduction in the overall time required to bring a service from development to production deployment, relative to comparable efforts performed through manual processes. This modularity allows the entire framework to be customized and integrated into larger systems, especially in a DevSecOps context where flexibility and extensibility are crucial. Finally, the paper provides both technical insights and practical benchmarks, offering a comprehensive solution for organizations seeking to optimize cloud service deployment pipelines using advanced NLP techniques.
See publication
Tags: Cybersecurity, DevOps, Generative AI
Establishing Design Routines for Efficient Control of Automated Robots
Young Scientists Convention
March 11, 2012
With continual advancements in technology, efforts to develop robots simulating human behavior have intensified. Cognitive robotics, combined with artificial intelligence (AI), has proven effective in surveying and research analysis. However, despite progress, human intervention remains necessary, and incorporating AI into robotic systems continues to pose challenges. This paper explores methodologies to integrate AI into robotic designs, aiming to enhance human-robot interactions. Several approaches are proposed to improve robotic performance, including routines for efficient control in varied environments and the incorporation of digital image processing for enhanced line-of-sight capabilities. A key contribution of this work is testing robotic systems in real-time environments to assess efficiency relative to existing models. Additionally, the paper introduces a robotic system with universal control capabilities, suitable for industrial applications, developed and programmed on the Arduino platform. Features such as GPS control for safe operations and progressive memory algorithms for efficient memory management are presented, offering advancements in both industrial and research applications.
See publication
Tags: Emerging Technology, Robotics, AI
Leveraging Large-Language Models based Machine Learning for Sentiment Analysis and Regional Consumer Insights in Amazon Product Reviews
Journal of Computational Analysis and Applications
December 09, 2024
In this paper, we use advanced NLP techniques and GPT based model, to analyze Amazon
product reviews and gain actionable insights. Amongst the models chosen, DistilBERT was
used as the feature extractor, BiLSTM for sentiment analysis and XGBoost for regional trend
prediction was used to develop and evaluate a hybrid model. With an accuracy of 92.3% for
positive insights and 87.6% for negative insights, the model proves to be reliable in
understanding consumer sentiment. The F1 scores, particularly 90.5% for positive and 84.9%
for negative insights, highlight its balance between precision and recall, ensuring that most
relevant instances are correctly classified. Additionally, the low Mean Absolute Error (0.077
for positive and 0.124 for negative) further validates the model's capability to minimize
prediction errors.
Further, as a case study, we identified regional variations in customer sentiment for a portable
Bluetooth speaker. The region-specific trend analysis reveals that the East Coast demonstrates
the highest preference for the product, with approximately 70% positive reviews, indicating
strong customer satisfaction in this region. On the other hand, the South Region exhibits the
lowest positive reviews (~18%) and the highest proportion of negative reviews, highlighting
significant dissatisfaction. The sentiment analysis from the analysis and predictions of the
regional trend translates into marketing strategies and product improvement, especially in
southern region to focus on sound quality and in rural markets where connectivity and battery
performance need to be addressed. This approach demonstrates the promise of combining state
of the art NLP techniques along with GPT to better understand customer preferences and
support product development and marketing decisions.
See publication
Tags: Emerging Technology, Generative AI, Predictive Analytics
The evolution of volumetric video: A survey of smart transcoding and compression approaches
International Journal of Computer Graphics & Animation (IJCGA) 2024
November 16, 2024
Volumetric video, the capture and display of three-dimensional (3D) imagery, has emerged as a revolutionary technology poised to transform the media landscape, enabling immersive experiences that transcend the limitations of traditional 2D video. One of the key challenges in this domain is the efficient delivery of these high-bandwidth, data-intensive volumetric video streams, which requires innovative transcoding and compression techniques. This research paper explores the state-of-the-art in volumetric video compression and delivery, with a focus on the potential of AI-driven solutions to address the unique challenges posed by this emerging medium.
See publication
Tags: AR/VR, Cloud, Generative AI
Physics Based Differentiable Rendering for Inverse Problems and Beyond
Journal of Electrical Systems
November 07, 2024
Physics-based differentiable rendering (PBDR) has become an efficient method in computer vision, graphics, and machine learning for addressing an array of inverse problems. PBDR allows patterns to be generated from perceptions which can be applied to enhance object attributes like geometry, substances, and lighting by adding physical models of light propagation and materials interaction. Due to these capabilities, distinguished rendering has been employed in a wider range of sectors such as autonomous navigation, scene reconstruction, and material design. We provide an extensive overview of PBDR techniques in this study, emphasizing their creation, effectiveness, and limitations while managing inverse situations. We demonstrate modern techniques and examine their value in everyday situations.
See publication
Tags: Emerging Technology, Engineering
Secure-by-Design AI Agents: Open-Source Workflows for DevSecOps Automation
ACM Austin
June 12, 2025
AI agents are evolving beyond prototypes and entering the software development lifecycle. In this talk, we’ll explore how to build a secure, intelligent agent that automates DevSecOps tasks—like scanning IaC for misconfigurations, detecting vulnerable dependencies, and auto-generating JIRA issues.
Using Python, LangChain, Trivy, and Semgrep, Hariharan will walk through how these tools can be orchestrated in a self-improving control loop that not only performs security checks but also learns and adapts.
Key Takeaways:
AI agents can enhance security workflows—not just chat experiences
Open-source tools are production-ready for agentic automation
LangChain can coordinate planning and execution—not just LLM prompts
Build reusable frameworks, not brittle scripts
See publication
Tags: Agentic AI, DevOps, IT Leadership
C++ and Python: Building Robust Applications by Offloading Compute-Heavy Workloads
Conf42
February 06, 2025
See publication
Tags: Cloud, Engineering, Leadership
Securely Unifying Deployments in an Organization for Increased Governance
Conf42
January 23, 2025
See publication
Tags: DevOps, IT Leadership, IT Strategy
Uncovering 100K Security Violations: Strengthening Application Security through Unified Deployments, XRAY Integration and Automated SBOM Generation
OWASP Foundation
April 05, 2025
In today’s application security landscape, navigating complex deployment environments often feels like facing an onslaught of cyber adversaries. Much like Batman’s trusty utility belt—equipping with the perfect gadget for every challenge—integrating robust security into your SDLC; transforms your pipeline into a resilient defense against vulnerabilities and breaches. This talk deep dives into a comprehensive case study where we revolutionized our security posture. On one hand, we applied an innovative strategy to unify all our deployments to 'Unified Deployment Model' based on Elastic Kubernetes Service (EKS), while on the other by integrating JFrog XRAY into each stage of our Software Development Lifecycle (SDLC). Through this integration, our team uncovered about 100K previously undetected security violations, that our traditional fragmented approach had overlooked. When dealing with large codebases comprising of several services, including client-side applications such as mobile and front-end, the lack of standardization, common-tooling causes increased operational burden, where-in multiple teams cook various in-house implementations for deployment. This causes two waves of problems. One there is no consistent approach to "shift-left" to have a faster feedback cycle. On the other hand – there is no means to have a uniform security posture, compliance and quality across the board. These make it challenging to get visibility on key metrics such as DORA metrics, due to the distributed and divergent nature of the pipelines across varied tech-stacks. Here, we'll explore approaches for architecting a 'Unified Deployment Pipeline' that accelerates developer velocity and productivity while enforcing robust security governance across the SDLC with integrated logging, tracing, and metrics. Additionally, by automating SBOM generation, our strategy delivers an organization-wide impact—enhancing transparency, compliance, and overall risk mitigation. This architecture also provides central observability of progress and aggregates metrics to monitor the health and maturity of deployments. Additionally, we will also investigate how the “Build Once, Deploy Many times” paradigm aligns with the proposed architecture. If you are a software engineer operating in the DevSecOps space, this talk aims at providing a high-level architecture for a unified end-to-end CICD pipeline that can help deploy services to production faster with greater confidence and better visibility, while being secure, compliant and deployed in a standardized manner. Hope this serves as a compelling blueprint for organizations looking to bridge the gap between innovative security practices and scalable, high-quality software delivery. Top takeaways: • Integration Strategy: How embedding XRAY into our unified deployment pipeline transformed our vulnerability management process. • Operational Impact: A deep dive into the metrics—over 100K security violations detected, reduced deployment times, and enhanced quality control—that validate the effectiveness of our approach. • Automated Compliance: The role of daily SBOM generation in maintaining transparency, ensuring regulatory compliance, and promoting rapid vulnerability remediation. • Lessons Learned: Challenges encountered during integration, the iterative improvements made along the way, and best practices for adopting a similar framework in diverse operational settings. Notes: 1. The aim is to show practical, architecture-level guidance that viewers can adapt. Additional code samples and diagrams will be provided as supporting materials. 2. This session is geared toward professionals with an intermediate to advanced understanding of DevSecOps practices, while still providing a foundational overview for newcomers 3. Beyond just theory, we’ll delve into practical tooling: incorporating OWASP-based scanning tools for code and dependency checks, embedding code-quality linters into the pipeline, and adopting runtime security scanning to prevent vulnerabilities from slipping into production. We’ll examine how OpenTelemetry can be used for distributed tracing, structured logging, and metrics collection, ensuring that each deployment is both transparent and auditable. 4. This session will provide the high-level guidance and practical insights needed to streamline end-to-end CI/CD pipelines and enhance overall reliability, visibility, and velocity.
See publication
Tags: Cybersecurity, DevOps, Security


 Template for Backtracking Problems — (Part1: The Basics)
Template for Backtracking Problems — (Part1: The Basics)
 Publisher-Subscriber model fundae
Publisher-Subscriber model fundae

