 Certified Information Systems Security Professional (CISSP)
Certified Information Systems Security Professional (CISSP)
ISC2
September 25, 2024
The vendor-neutral CISSP credential confirms technical knowledge and experience to design, engineer, implement, and manage the overall security posture of an organization. Required by the world’s most security-conscious organizations, CISSP is the gold-standard information security certification that assures information security leaders possess the breadth and depth of knowledge to establish holistic security programs that protect against threats in an increasingly complex cyber world.
See publication
Tags: Security
 Cybersecurity Exam Development Volunteer
Cybersecurity Exam Development Volunteer
ISC2
March 27, 2023
Professionals who earn this badge have volunteered to serve in ISC2 exam development workshops. These certified cybersecurity professionals have written, revised, and/or reviewed exam items for the certification they hold. During exam development workshops, professionals update exam outlines and participate in standard setting.
See publication
Tags: Cybersecurity, Security
 Fundamentals for eBPF by Solo.io
Fundamentals for eBPF by Solo.io
Solo.io
March 09, 2023
eBPF (Extended Berkeley Packet Filter) is a revolutionary Linux technology that can run sandboxed programs in an operating system kernel to safely and efficiently extend the capabilities of the kernel without requiring changes to kernel source code or load kernel modules. In this workshop, you will learn about eBPF and the different ways to create eBPF programs, create your first eBPF program using BCC and libbpf, build and deploy an eBPF program with BumbleBee, and more.
See publication
Tags: Cloud, Cybersecurity
 Certified in Cybersecurity (CC)
Certified in Cybersecurity (CC)
ISC2
October 27, 2022
The vendor-neutral CC credential starts newcomers on their path to advanced cybersecurity certifications and future leadership roles. It proves to organizations that newly certified team members understand fundamental security principles and operations, network security and access controls and that they have the skills to meet and exceed performance standards in their beginning roles. All this allows organizations to build a stronger line of defense
See publication
Tags: Cybersecurity, Security
 LFS253: Containers Fundamentals
LFS253: Containers Fundamentals
The Linux Foundation
January 29, 2022
Earners of the LFS253: Containers Fundamentals badge have a good understanding of container technologies. They are able to do container and image operations with different container runtimes, manage network and storage (volumes) with containers, as well as build and run multi-container applications with Docker and Docker APIs.
See publication
Tags: Cybersecurity, Security
 Microsoft Certified: Azure Fundamentals
Microsoft Certified: Azure Fundamentals
Microsoft
May 10, 2021
Earners of the Azure Fundamentals certification have demonstrated foundational level knowledge of cloud services and how those services are provided with Microsoft Azure.
See publication
Tags: Cloud, Cybersecurity
CKS Exam Tips and Tricks: Mastering CLI and Vim for Success
Medium
September 06, 2025
The Certified Kubernetes Security Specialist (CKS) exam is a hands-on, performance-based test conducted entirely via the command line. You will face 15–20 tasks to solve within 2 hours . It’s a remotely proctored exam, and you must already be CKA-certified (Certified Kubernetes Administrator) before taking CKS .
See publication
Tags: Cloud, Cybersecurity, Security
Mastering Quectel Modem Troubleshooting with qmicli
Medium
September 06, 2025
Troubleshooting modem issues on Linux with qmicli can range from simple connectivity problems to more complex challenges like ‘OutOfCall’ and ‘UimUninitialized’ errors. This advanced guide expands on basic troubleshooting steps, providing a comprehensive approach to resolving both common and intricate issues.
See publication
Tags: Cloud, Cybersecurity, Security
 Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond
Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond
Medium
September 06, 2025
Telecom has never lacked ambition. 5G network slicing was pitched as the key to entirely new business models. Remote robotic surgery over 5G was supposed to revolutionize healthcare. Cloud-Native adoption in 5G promised to bring the agility of web-scale companies to mobile networks.
See publication
Tags: Cloud, Cybersecurity, Security
Tips and Tricks for Preparing for Behavioral Interviews
Medium
October 03, 2024
Hey there! Preparing for a behavioral interview might feel a bit daunting, but with some thoughtful preparation, you can walk in feeling confident and ready to impress.
See publication
Tags: Cloud, Cybersecurity
Setting Up a Data Connection via QMI Interface on Raspberry Pi with Quectel Modem and Sixfab Shield
Medium
November 06, 2023
When working with Raspberry Pi in areas without traditional internet access, cellular connectivity becomes a lifeline. For robust communication, the QMI (Qualcomm MSM Interface) is often the go-to choice for interfacing cellular modems like the Quectel EG25-G, especially when paired with a Sixfab development board. This post will guide you through setting up a data connection over the QMI interface using the libqmi library, specifically tailored for the Quectel modem.
See publication
Tags: Cloud, Cybersecurity
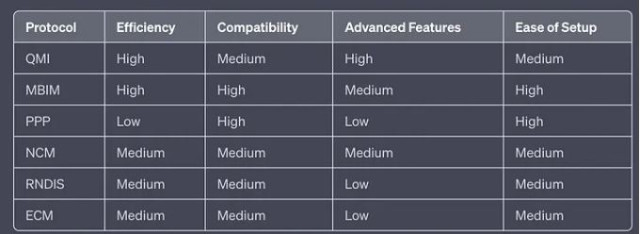 Unveiling Cellular Connectivity with Raspberry Pi: A Journey through 4G/LTE/5G Modem Protocols
Unveiling Cellular Connectivity with Raspberry Pi: A Journey through 4G/LTE/5G Modem Protocols
Medium
November 02, 2023
In the flourishing domain of IoT and edge computing, the requirement for steadfast, high-speed internet connectivity is indispensable. The Raspberry Pi, with its adaptable and compact nature, melds seamlessly with contemporary 4G/LTE and 5G modems to fulfill this requirement. This harmonization is chiefly navigated through several prevalent protocols that mediate the interaction between the hardware and cellular networks. In this discourse, we delve into these protocols with a spotlight on QMI, MBIM, and PPP, which are the frontrunners in this space.
See publication
Tags: Cloud, Cybersecurity, IoT
Understanding Link-Local Addressing and Its Role in SD-WAN Overlays
Medium
June 16, 2023
When we think of IP addressing, the public and private IP address spaces probably come to mind. But there’s another category of IP addresses that plays an important role in networking: link-local addresses. They’re particularly useful in Software-Defined Wide Area Networks (SD-WANs) and the creation of overlay networks. In this blog post, we’re going to delve into the world of link-local addressing and understand how it’s leveraged in SD-WAN overlays
See publication
Tags: Cloud, Cybersecurity
 Turning Your Raspberry Pi into a Mobile Hotspot Bridge: A Step-by-Step Guide
Turning Your Raspberry Pi into a Mobile Hotspot Bridge: A Step-by-Step Guide
Medium
May 17, 2023
Imagine you’re in a situation where you only have a mobile hotspot for internet access, but you need to provide a wired LAN connection for a device that doesn’t support Wi-Fi. It might sound like a tricky problem, but it’s actually something a Raspberry Pi can handle with ease! This guide will walk you through how to turn your Raspberry Pi into a bridge between a mobile hotspot and a wired LAN connection.
See publication
Tags: Cloud, Cybersecurity
 Installing Podman on Macbook
Installing Podman on Macbook
Medium
April 19, 2023
Here are the steps to get started with Podman on a MacBook
See publication
Tags: Cloud, Cybersecurity


 Certified Information Systems Security Professional (CISSP)
Certified Information Systems Security Professional (CISSP)
 Cybersecurity Exam Development Volunteer
Cybersecurity Exam Development Volunteer
 Fundamentals for eBPF by Solo.io
Fundamentals for eBPF by Solo.io
 Certified in Cybersecurity (CC)
Certified in Cybersecurity (CC)
 LFS253: Containers Fundamentals
LFS253: Containers Fundamentals
 Microsoft Certified: Azure Fundamentals
Microsoft Certified: Azure Fundamentals
 Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond
Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond
 Unveiling Cellular Connectivity with Raspberry Pi: A Journey through 4G/LTE/5G Modem Protocols
Unveiling Cellular Connectivity with Raspberry Pi: A Journey through 4G/LTE/5G Modem Protocols
 Turning Your Raspberry Pi into a Mobile Hotspot Bridge: A Step-by-Step Guide
Turning Your Raspberry Pi into a Mobile Hotspot Bridge: A Step-by-Step Guide
 Installing Podman on Macbook
Installing Podman on Macbook
 Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond
Open RAN’s Collapse and the 6G Hype Cycle: Lessons for AI-RAN and Beyond Mastering Quectel Modem Troubleshooting with qmicli
Mastering Quectel Modem Troubleshooting with qmicli CKS Exam Tips and Tricks: Mastering CLI and Vim for Success
CKS Exam Tips and Tricks: Mastering CLI and Vim for Success