Mar23

By 2025, cybercrime will cost the global economy $10.5 trillion annually—a figure surpassing the GDP of most nations. Yet, as businesses race to adopt cloud platforms, AI, and remote work tools, their defenses often lag behind. From the SolarWinds breach to AI-driven phishing farms, modern threats demand a paradigm shift in cybersecurity strategy. Here’s how organizations can pivot from reactive to proactive defense.
The Risk:
The surge in cloud adoption (web hosting market to hit $183B by 2026) and remote work has centralized data into sprawling digital vaults. But centralized data is a bullseye:
The Solution:
Key Stat: 68% of breaches involve credential misuse (Verizon DBIR 2023).
The Threat:
Cybercriminals now operate like Fortune 500 firms, leveraging AI to scale attacks:
The Defense:
Case Study: A European bank thwarted a deepfake CEO fraud attempt using AI voice biometrics.
The Challenge:
The Fix:
Stat: Companies using SBOMs saw 60% faster breach response (Gartner).
Pro Tip: The NSA’s Cybersecurity Collaboration Center offers free frameworks for critical infrastructure.
The future of cybersecurity isn’t about building higher walls—it’s about predicting where the next ladder will appear. From Zero-Trust to AI-augmented SOCs, survival hinges on staying two steps ahead of adversaries who never sleep.
Keywords: Cloud, IT Strategy, Security
 Lateral Moves: The Most Overlooked Succession Strategy in Companies
Lateral Moves: The Most Overlooked Succession Strategy in Companies The Asset Play: Timing, Structure & Global Arbitrage
The Asset Play: Timing, Structure & Global Arbitrage 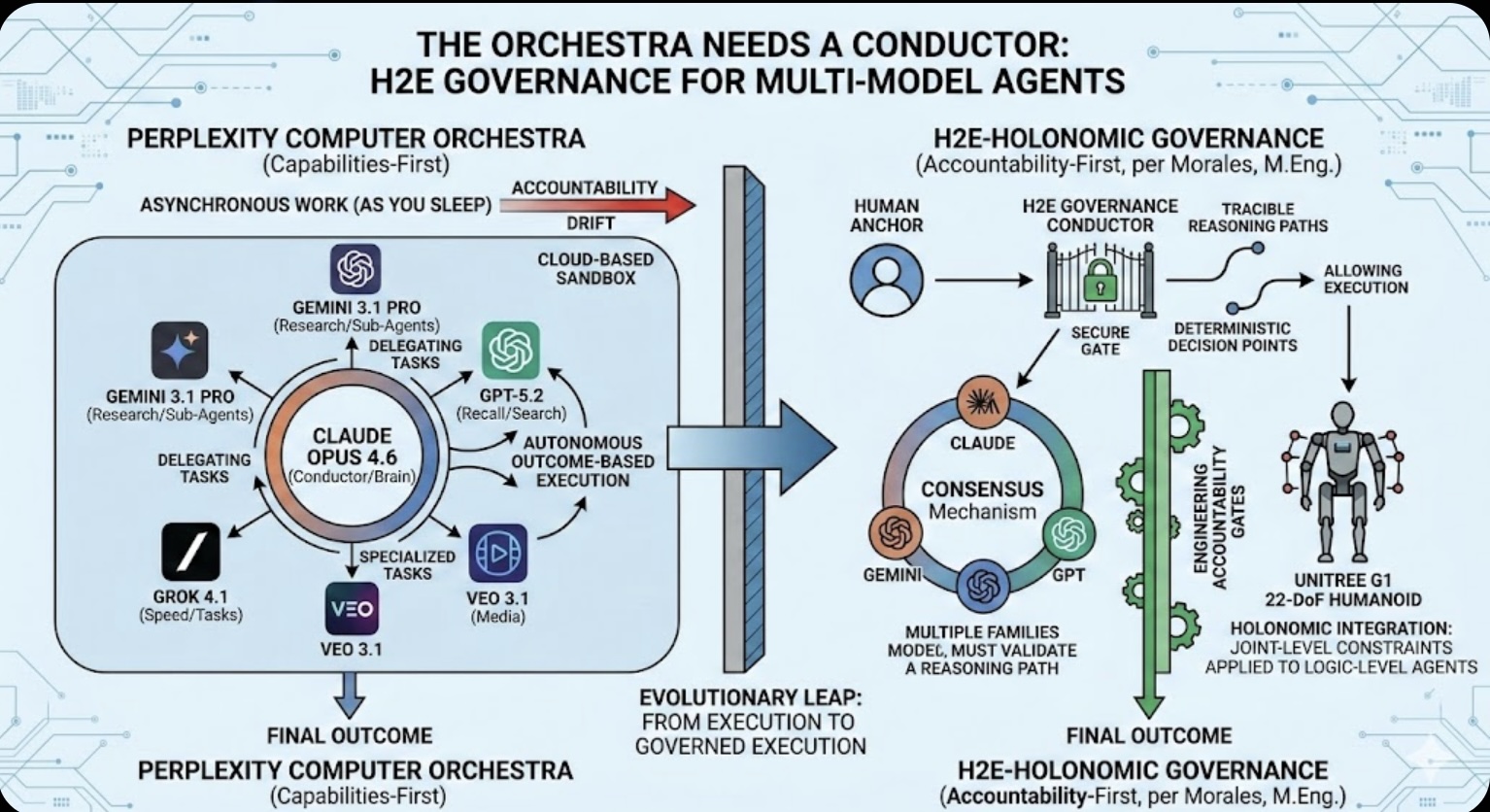 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business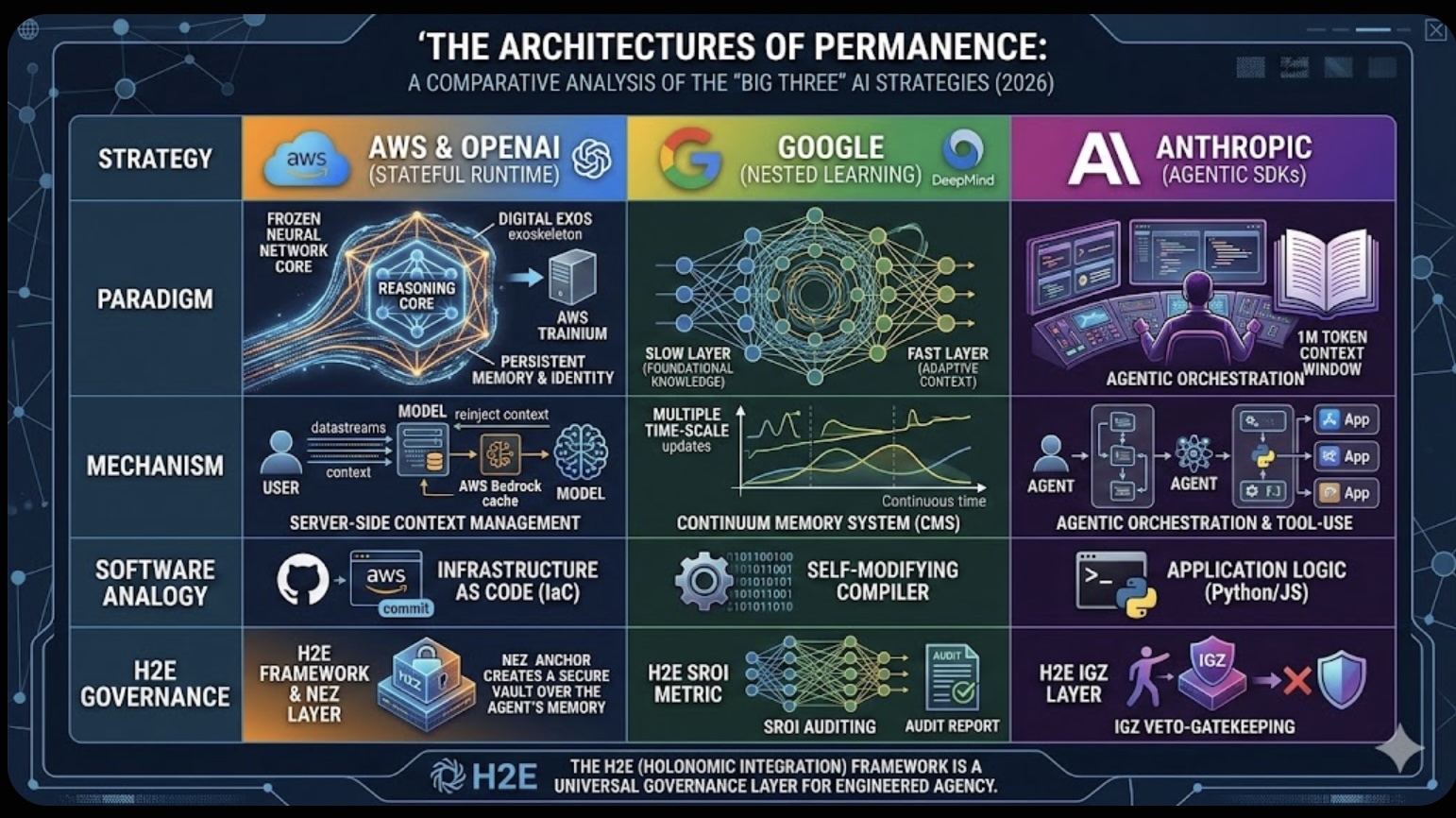 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)