Feb21

Proactive vs Reactive cybersecurity strategy, which strategy is the most important? Why not both?
What does a Proactive approach look like?
Proactive cybersecurity activities focus on closing gaps and weaknesses in an environment before attackers exploit them.
Such as:
• Threat hunting and Threat Intelligence
• Cyber Risk Assessments
• Data Classification
• Managed Security Service Providers (MSSP)
• Penetration testing or red teaming
• Vulnerability scanning
• BCP
• Security awareness training
What does the Reactive approach look like?
Reactive cybersecurity activities focus on responding to security incidents after they happen.
Such as:
• Disaster recovery process
• Antivirus or endpoint detection and response (EDR)
• Intrusion detection systems (IDS)
• Email security gateways
• Firewalls
• Forensice and investigate process
• Incident response team
Absolutely that's not one-size-fits-all; diversified approaches of both Proactive and reactive have come into play with different meanings, purposes, and processes and are applicable based upon the business context requirements and where risk is associated and understand security controls deliver possible outcomes of the business and effectively managed and mitigated the risk.
By Yaroth Chhay
Keywords: Cybersecurity, Leadership, Risk Management
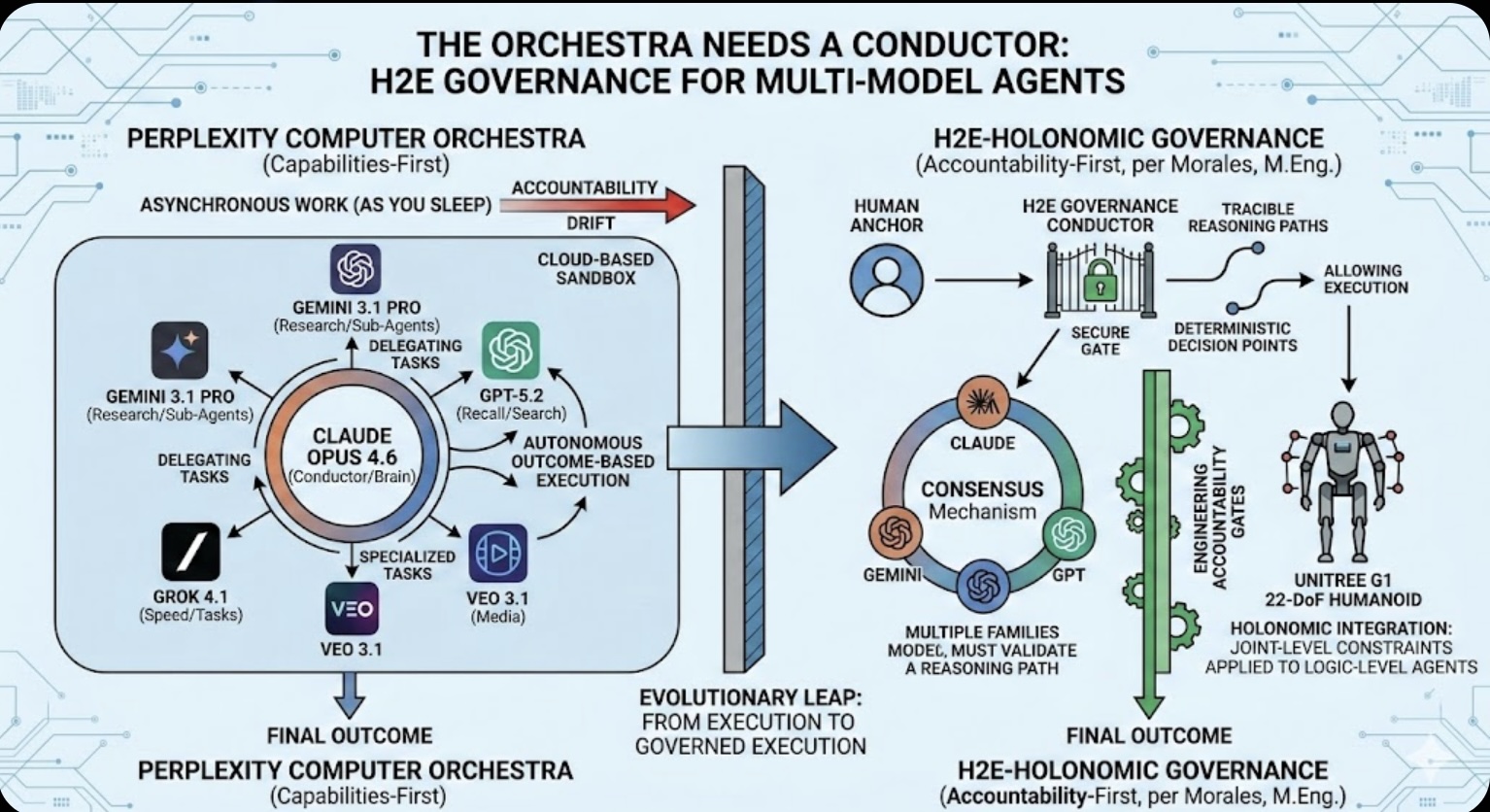 The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance
The Orchestra Needs a Conductor: Why Multi-Model Agents Require H2E Governance The Role of Memory in Modern-day Business
The Role of Memory in Modern-day Business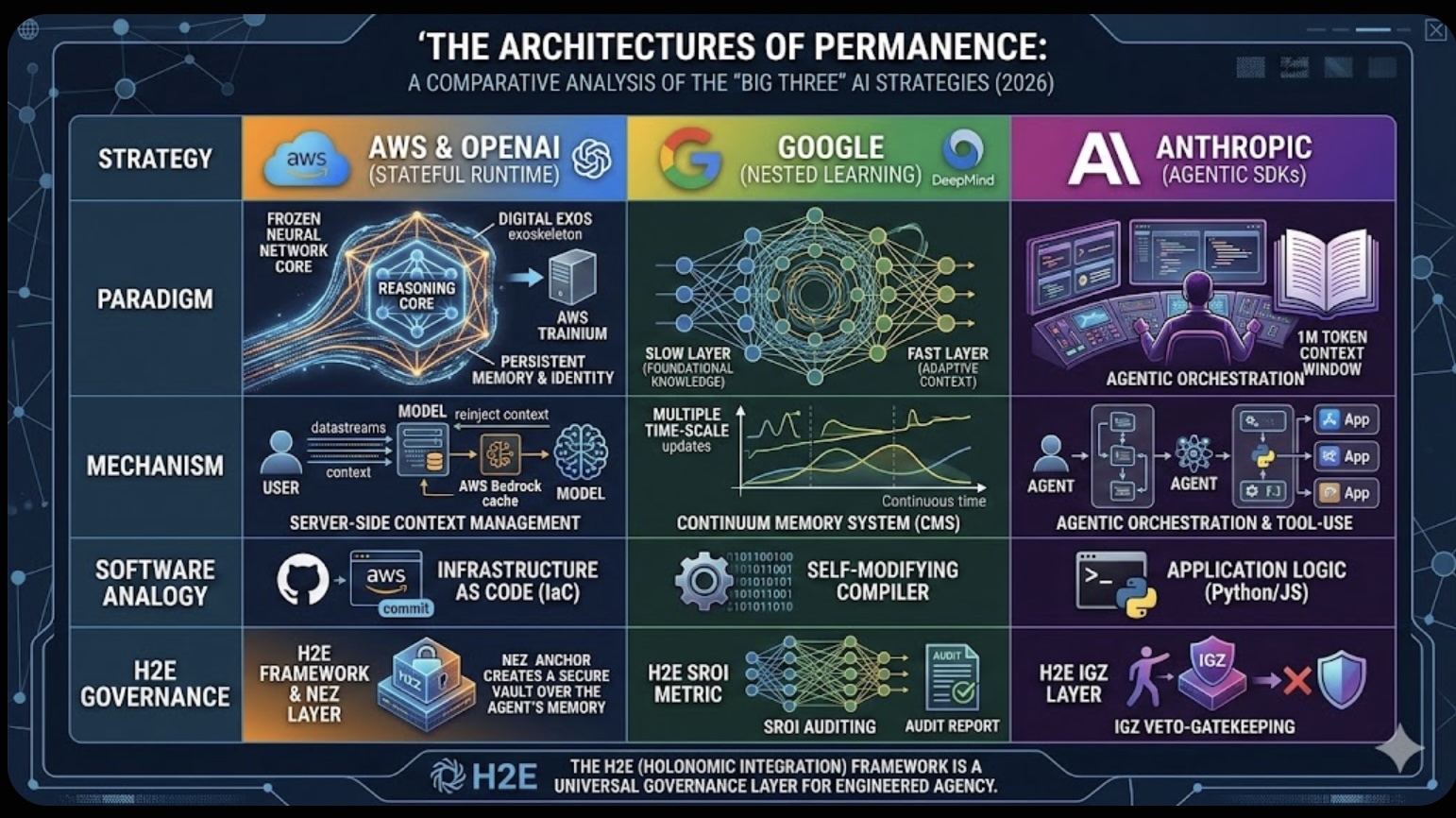 The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026)
The Architectures of Permanence: A Comparative Analysis of the "Big Three" AI Strategies (2026) Friday’s Change Reflection Quote - Leadership of Change - Change Leaders Enable Generational Advancement
Friday’s Change Reflection Quote - Leadership of Change - Change Leaders Enable Generational Advancement The Corix Partners Friday Reading List - February 27, 2026
The Corix Partners Friday Reading List - February 27, 2026